You, your network and the Locky virus
Last Monday, a new particularly clever (and nasty) piece ransomware appeared on the internet called Locky.
The malicious file went undetected by most anti-virus software for a number of days and even now a couple weeks since it appeared, antivirus products are still struggling to keep up, often taking upto 24 hours to include detection in their definition packages for each new daily iteration version of the virus.
This clearly has left users and company network exposed.
How it works :
It is initially spread through a Word doc embedded in an email. He is an example of one of those emails:
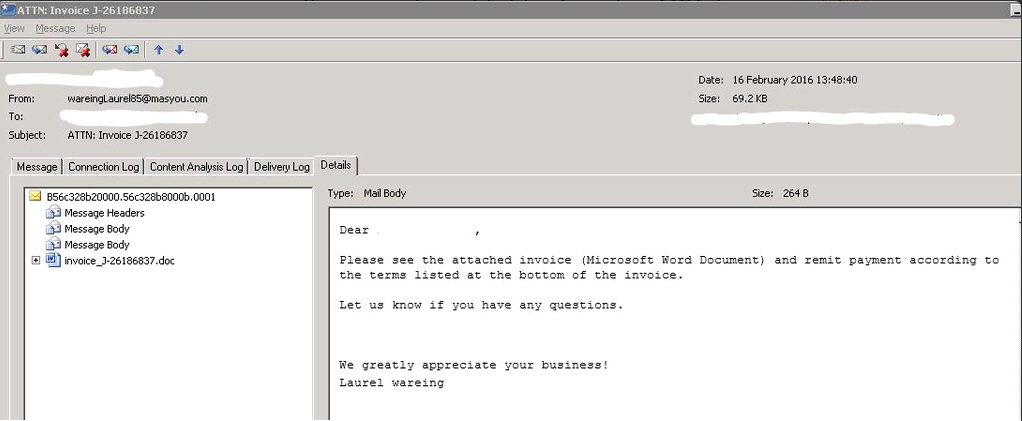
Attached to this email is a Word document containing an alleged Invoice.
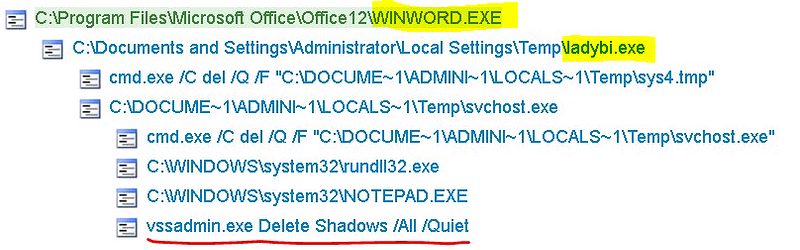
If Office macros are enabled on this document – it unleashes an executable called : ‘ladybi.exe’
This loads itself into memory then deletes itself. Whilst resident in memory – it encrypts your documents as hash.locky files, changes the desktop wallpaper, creates a .bmp file and opens it, creates a .txt file and opens it, and delete VSS snapshots. It can also reach out and encrypted files on your company network!
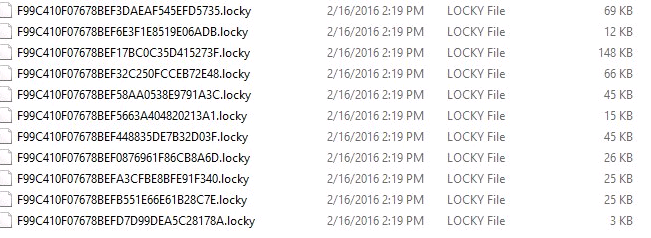
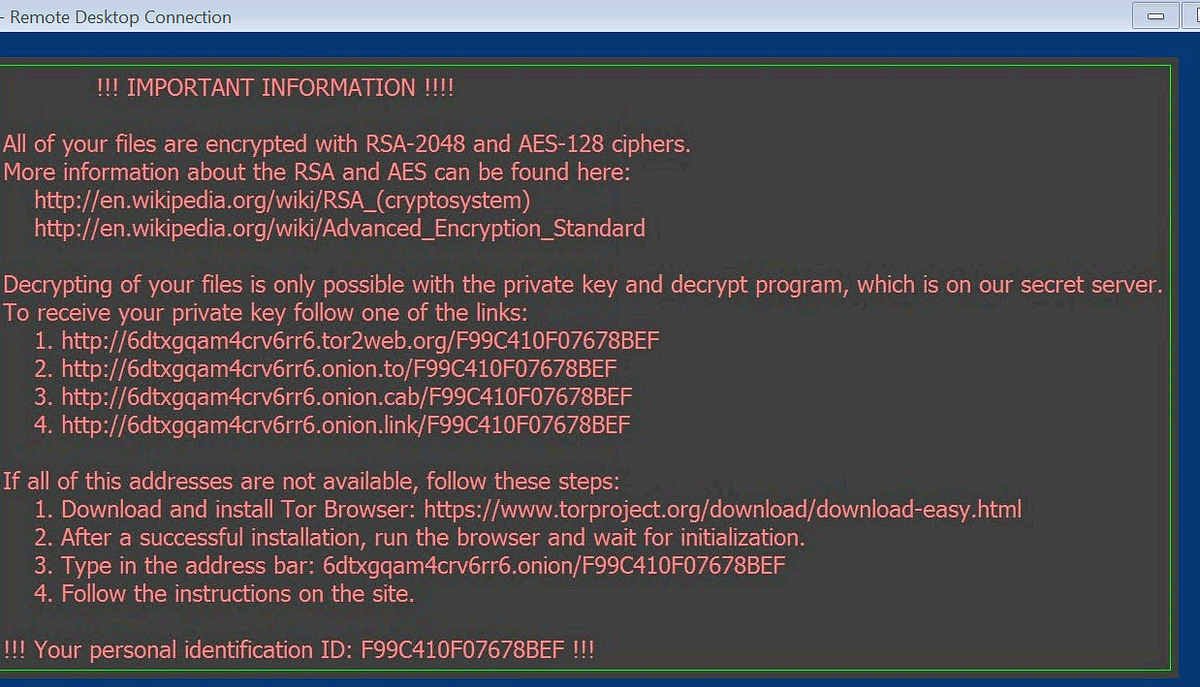
Once the files are encrypted, a ransom demand appears on the PC directing the user towards the the ‘Deep Web‘ to make a payment in Bitcoin to get your files decrypted.
Recovery
To recover your files you need to rely on you backups. It is thought unlikely that any kind of tool will become available to break the encryption algorithms. We do not recommend paying ransoms.
Identifying infected network users
If you see .locky extension files appearing on your network shares, look up the file owner on _Locky_recover_instructions.txt file in each folder. This will tell you the infected user. Lock their AD user and computer account immediately and boot them off the network — you will likely have to rebuild their PC from scratch.
Prevention
User education – do not open emails from unknown sources!
Disable Macro’s in office documents – this can be done on a network level via Group Policy
Global spread
The deployment of Locky was a masterpiece of criminality — the infrastructure is highly developed, it was tested in the wild initially on a small scale (ransomware beta testing, basically), and the ransomware is translated into many languages. In short, this was well planned and expertly executed.
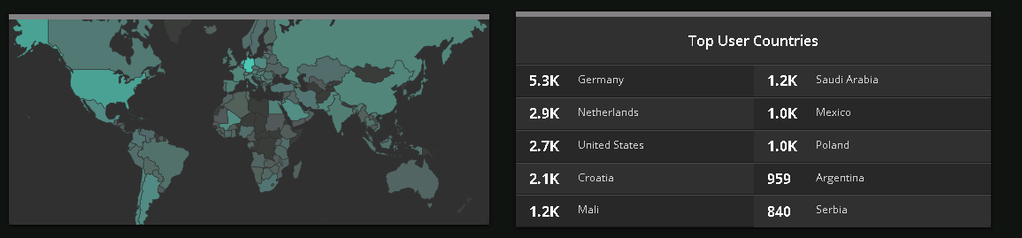
One hour of infection stats
Measuring the impact
Locky contains code to spread across network drives, allowing the potential to impact large enterprises outside of individual desktops.
Twitter impressions of over half a million this week from talking about this. It is thought many organisations are simply paying for the decrypter, which is basically paying your hostage takers for freedom. It’s also worth noting that many of the IP addresses getting hit by this are associated with addresses at large companies, many in the US; this clearly caught people out.
Sources:
https://medium.com
http://www.idigitaltimes.com
