Social Media Malware is Deviant, Destructive
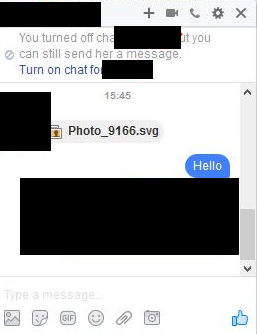
We’ve seen some tricky techniques used by cybercriminals to distribute malware through social media. One common threat begins with a previously compromised Facebook account sending deceptive messages that contain SVG image attachments via Facebook Messenger. (The SVG extention is an XML-based vector image format for two-dimensional graphics with support for interactivity and animation.)
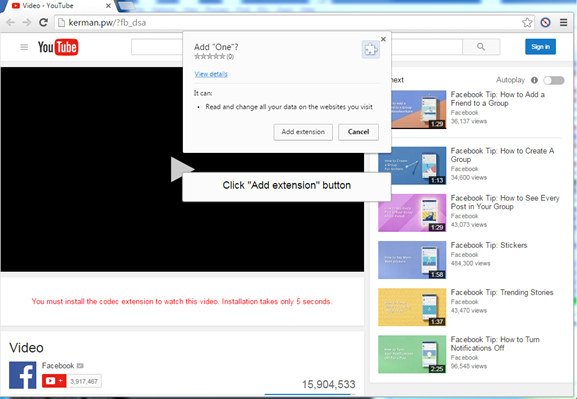
Cybercriminals prefer this XML-based image as it allows dynamic content. This enables the criminals to add malicious JavaScript code right inside the photo itself—in this case, linking to an external site. Users who click on the image find themselves on a website posing as YouTube that pushes a popup to install a browser extension or add-on or to view a video. There are plenty of red flags here like the URL clearly not being YouTube.com, as well as the fact that YouTube does not require any extensions to view videos.
Worm-like propagation
If a you were to install this extension, it will take advantage of your browser access to your Facebook account to secretly mass-message your friends with the same SVG image file—like a worm, this is how it spreads. Victims don’t need to have very many friends for this tactic to be successful at propagating. For instance, if you have over 100 friends, then you only need less than 1% of your friends to fall for this for the scam for it to continue to propagate.
To make matters worse, the extension also downloads Nemucod, a generic malware downloader generally used to download and install a variety of other threats. Usually the go-to threat is ransomware given it’s proven business model for criminals.
Social media managers at risk
Those who manage social media accounts on behalf of businesses are particularly at risk of advanced malware and other cyberattacks. Earlier this spring, a new Windows trojan dubbed Stresspaint was found hidden inside a fake stress-relief app and likely spread through email and Facebook spam campaigns to infect 35,000 users, according to researchers at Radware who discovered the malware.
Stresspaint was rather deviant in the way it stole Facebook account credentials and logged into accounts looking specifically for data such as “each user’s number of friends, whether the account manages a Facebook Page or not, and if the account has a payment method saved in its settings,” according to Bleeping Computer.
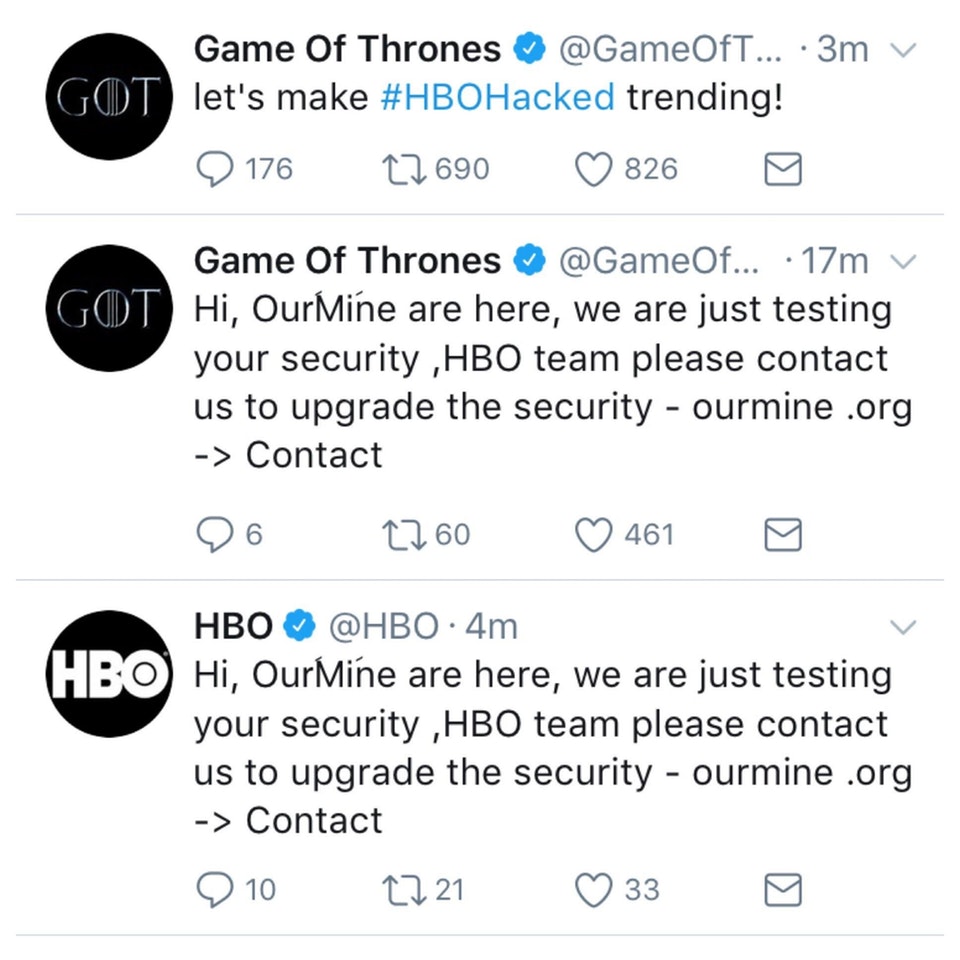
Allowing cybercriminals to gain control of brand social media accounts can carry grave consequences such as reputation damage, loss of confidential information, and deeper access into an organization’s network. Last year, HBO was humiliated on their social profiles when the notorious hacker group OurMine breached several the network’s accounts and posted messages before the company finally regained control of their logins.
Crypto users targeted
Following the recent trend in malware, sophisticated variants of existing strains are now aimed at cryptocurrency users. A malicious Google Chrome extension called FacexWorm, which spreads through Facebook Messenger, was found to have morphed with a new ability to hijack cryptocurrency transactions made on a host of popular online exchanges, according to Coindesk. This further underlines the importance of exercising caution with the information you share on social media to avoid being a target, particularly if you are a user of cryptocurrency.
Cryptocurrency scams are another common threat that spreads throughout social media. Twitter is particularly notorious an outbreak of crypto scam bots that pose as high-profile tech leaders and industry influencers. Learn more about this type scam in my previous post.
Don’t let your guard down
Given the nature of social networks, many are likely to consider themselves to be in the company of friends on sites like Facebook, Instagram and Twitter. However, this assumption can be dangerous when you begin to trust links on social sites more than you would in your email inbox or other websites. For instance, a simple bot-spam message on Twitter was able to grant a hacker access to a Pentagon official’s computer, according to a New York Times report published last year.
It’s wise to be wary of clicking on all links, even those sent by friends, family or professional connections, as compromised social media accounts are often used to spread scams, phishing, and other types of cyberattacks. After all, just one wrong click can lead to an avalanche of cyber woes, such as identity theft, data loss, and damaged devices.
This article was provided by our service partner : webroot.com