Managed Services 101: Where MSPs Are Now, and Where They’re Going
Managed services are becoming an increasingly integral part of the business IT ecosystem. With technology advancing at a rapid pace, many companies find it cheaper and more effective to outsource some or all of their IT processes and functions to an expert provider, known as a managed service provider (MSP).
Unlike traditional on-demand IT outsourcing, MSPs proactively support a company’s IT needs. And with the IT demands of businesses becoming ever more complex, reliance on MSPs is likely to increase exponentially over the next few years.
What Is a Managed Service Provider?
An MSP manages a company’s IT infrastructure on a subscription-based model. MSPs offer continual support that can include the setup, installation, and configuration of a company’s IT assets.
Managed services can supplement a company’s internal IT department and provide services that may not be available in-house. And since the MSP is continuously supporting the company’s IT infrastructure and systems, rather than simply stepping in from time to time to put out a fire, these services can provide a level of peace of mind that other models just can’t match.
What’s the Difference Between Managed Services and the Break/Fix Model?
Unlike on-demand outsourced IT services, managed services play an ongoing and harmonious role in the running of an organization.
Due to the rapidly changing nature of the digital landscape, it’s no longer sustainable to fix problems after the damage is done. Yet the break/fix model in softwarre development companies like Software Development UK, is still a common way of dealing with IT-related problems. It’s like waiting to repair a minor leak until after the pipe has burst.
On-demand providers are usually brought in to perform a specific service (like fixing a broken server), and they bill the customer for the time and materials it takes to provide that service. MSPs, on the other hand, charge a recurring fee to provide an ongoing service. This service is defined in the service-level agreement (SLA), a contract drawn up between the MSP and the customer that defines both the type and standards of services the MSP will be expected to provide. This monthly recurring revenue (MRR) can provide a lucrative and reliable revenue stream.
What Services Can an MSP Provide?
MSPs provide systems management solutions, centrally managing a company’s IT assets. This encompasses everything from software support and maintenance to cloud computing and data storage. These solutions can be especially valuable for small- and medium-sized businesses (SMBs) that may not have robust internal IT departments, especially when it comes to hard-to-find skills.
Network Monitoring and Maintenance
From slow loading times to outages, inefficient and faulty systems can cost companies a fortune in lost productivity. MSPs reduce the likelihood of such delays by keeping an eye on the network for slow or failing elements. By using a remote monitoring and management (RMM) tool, the MSP will automatically be notified the moment an issue arises, allowing them to identify and fix the problem as quickly as possible. That means shorter downtime, so the customer’s tech—and the business needs it supports—can get up and running again in no time.
Software Support and Maintenance
MSPs provide software support and maintenance to ensure the smooth running of all business applications that a customer needs on a daily basis. This includes ensuring that the programs used to maintain the network are fully functional. Overall, the goal is to provide an uninterrupted experience so that work can carry on as normal.
Data Backup and Recovery
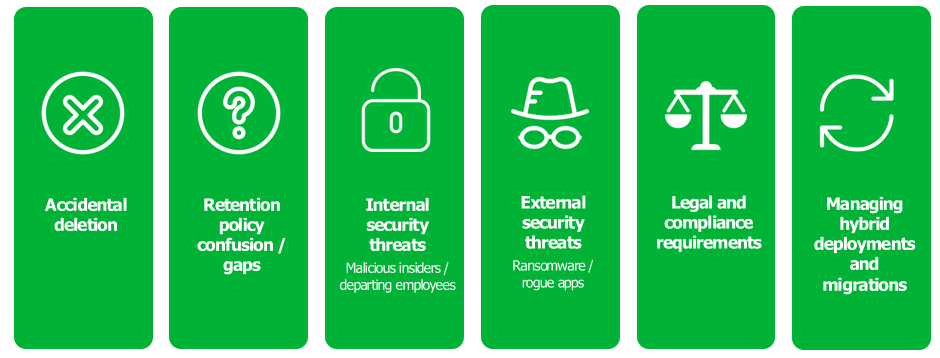
Data loss can be catastrophic, so companies need to have a system in place to back it up and recover it, should the worst happen. MSPs can handle the backup process, protecting companies against both accidental deletion and file corruption, or more malicious intent (like cyberattacks). They can also support a company’s overall disaster recovery plan, ensuring the business can always recover its data in the event of an emergency.
Data Storage
MSPs can also help their clients optimally store their data. While hard data storage was once standard, new forms of remote data storage are growing in popularity, including cloud computing. MSPs can enable seamless data migration if the client decides to switch storage options.
Cloud Computing
Cloud computing encompasses more than just remote data storage options. Various IT applications and resources can be accessed via online cloud service platforms, with providers charging a pay-as-you-go fee for access. Whether the client relies on a public, private, or hybrid cloud platform, MSPs can help them navigate the cloud successfully, streamlining their workflows, storing data successfully, and more.
Challenges Facing MSPs
While there are numerous benefits to the managed services model, including the recurring revenue and the ability to build long-lasting relationships with clients, this model isn’t without its challenges.
Shifts in Sales and Marketing
Until recently, many MSPs have grown organically through referrals and word of mouth. But increasingly, companies are seeing the value of the ‘master MSP’ model, which offers valuable infrastructure to other MSPs in areas where their own expertise may be lacking. As a result, we see a trend toward inorganic growth.
In this market, MSPs can stand out from the crowd by investing their efforts in product management. Prioritizing the needs of the customer is a simple way to create value around your services. This goes beyond the basic standards outlined in the service level agreement—it’s about showing you go above and beyond.
Keeping Existing Customers
With new differentiators emerging, MSPs have to adjust their approach to keep customers happy.
One way they can set themselves apart is by having business conversations very early on in the relationship. By gaining a clear understanding of the outcomes the client wants to achieve and working with them to come to an agreement surrounding expectations, MSPs can establish themselves as a partner rather than simply a provider. This will allow you to adjust your approach to match their needs—like driving for profit rather than acting as a cost center.
Best-in-class MSPs also rarely find themselves arguing with customers over whether something is covered. That’s because they’re fully aligned on what the MSP is responsible for. Whatever the SLA covers, it’s the MSP’s job to ensure their client understands. This requires regular conversations to confirm everyone is on the same page and satisfied. Documenting these conversations also allows MSPs to streamline any disagreements by showing what has been discussed and agreed upon. The goal is to become a trusted advisor that they turn to for guidance.
A next-level approach to proactivity is also a plus. This includes setting up alerts to rapidly identify issues and putting new measures in place to ensure mistakes don’t repeat themselves.
Transitioning toward a more risk-based approach, bolstered by a security-first mindset, will go a long way, opening doors for both more recurring and non-recurring revenue streams as clients seek out your consultation. The best MSPs are experts at assessing their customers’ environment and developing a tailored plan that covers governance, compliance, and ongoing risk management. What’s more, they adjust their approach regularly to reflect the ever-changing security needs of their clients—offering more opportunities to showcase their value and up their revenue stream.
The Impact of Cloud Computing
While MSP revenue is rising, profit margins are actually shrinking. Part of the problem is the fact that MSPs are expanding their portfolio of services, yet still relying on their former pricing structures. But many MSPs are making the problem worse by choosing the wrong cloud service vendor to partner with, which can significantly impact an MSPs already-shrinking profit margins.
Some cloud service vendors are simply not priced to support an MSP. And with the pace at which cloud technology is evolving, a process that was cutting-edge when an MSP implemented it could become inefficient within a period of weeks. It’s vital that MSPs be open to change if a vendor becomes unsustainable, lest risk their own services becoming unsustainable as a result.
You should also be ready to address any cloud-related questions and concerns that clients raise. Cloud technology is still relatively new, and it can be confusing, so overcoming any uncertainties will play a key role in an MSP’s ability to act as a valuable advisor to its clients.
How MSPs Use Software
Just as they bring value to their customers by streamlining workflows and protecting networks, MSPs need internal frameworks that increase efficiency.
Professional services automation (PSA) tools allow MSPs to streamline and automate repetitive administrative tasks. This saves time and cuts costs, all while enabling greater scalability.
MSPs can also utilize remote monitoring and management (RMM) tools. These automate the patching process and allow you to reduce time spent on resolving tickets, essentially doing more with less. Not only does this enable a more proactive approach, but it puts time back into the support team’s day to focus on other things.
Needless to say, MSPs should be easily accessible to their clients via technology. Remote desktop support makes that possible. With remote control over a client’s systems, MSPs can rapidly solve issues from wherever they are—without interfering with the end user’s access. This reduces customer downtime, allowing repairs and IT support to happen quietly in the background.
What the Future Holds for MSPs
The role of MSPs is changing. Keeping an eye on these emerging trends can help you anticipate shifting client expectations—and stay ahead of the curve.
Arguably the largest area of opportunity for MSPs is cybersecurity—and that service is only going to grow more valuable. Even as awareness increases and regulations tighten around data privacy laws, the number and complexity of cyberattacks continue to rise. Between 2017 and 2018, the annual cost of combating cybercrime rose by 12%—from $11.7 million to a record high of $13 million—so establishing yourself as a cybersecurity expert now will put you in good stead for the future.
The Internet of Things (IoT) is also going to have a major impact on MSPs. Keeping up with the sheer volume of devices being used on a day-to-day basis requires a dynamic approach to systems management. This includes being proactive about establishing best practices and security guidelines around new technology, such as the use of voice assistants.
Business intelligence offerings are also likely to grow in demand. With the use of IT in business at an all-time high, the amount of data being generated is enormous. But data is only numbers without someone to effectively consolidate and analyze it to extract actionable insights. Providing easy access to reports and KPIs that clearly demonstrate areas for improvement will allow MSPs to not only stay relevant in this data-driven market but become leaders in their field.
This article was provided by our service partner : connectwise.com