5 Cybersecurity Tips for Better 2020 Protection
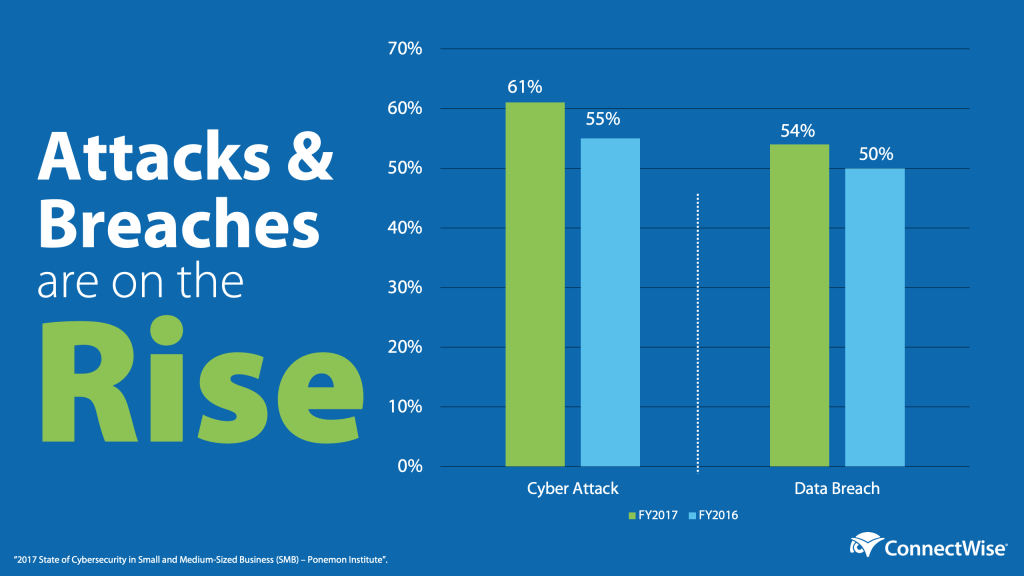
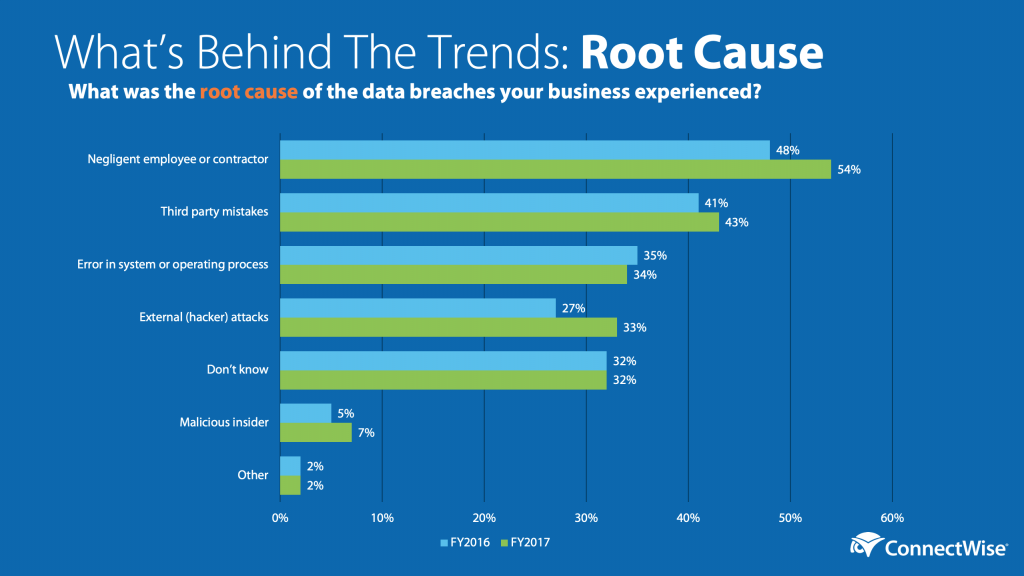
You couldn’t go a day in 2019 without hearing about another cybercriminal hitting a business or city, and 2020 will be more of the same. You’ve probably even had your fair share of conversations with your customers about what you’re doing to keep them and their data secure. It’s better to have the tough talks now and get a plan in place than try to make excuses for your lack of protection if your customers get hit. So, let’s get ready for 2020 together with these cybersecurity tips. Learn how incident response services can benefit and improve your business strategy.
1. Pay Attention to the Security Around APIs
Cybercriminals and their tactics are evolving and will continue to evolve. With new advancements in technology, attacks will go beyond the normal threat vectors. You can see Nettitude online for cybersecurity assistance
“There are still plenty of attack surfaces today in your traditional Windows® domain environments,” says Jon Murchison, CEO of Blackpoint Cyber. “As the shift starts to the cloud and as we open more APIs for automation, I think you’re going to see API-based attacks increase massively. Vendors need to pay attention as they open more of these things up, they’ll be turned against them.”
While the cloud and automation have made life easier for managed service providers (MSPs) and their customers, they also present an opportunity for cybercriminals to use that convenience against unsuspecting victims. When you’re looking at your security for 2020, you need to be aware of all the entry points into your network and your customers’ environments, which leads us to our next tip: enabling multi-factor authentication (MFA).
2. Enable MFA on Everything
Although it may seem like a minor inconvenience for end users, MFA is a small security measure that can have a significant impact on making sure the right people have access to networks and applications. MFA, or two-factor authentication (2FA), is an added layer of security that requires a user to present a second form of authentication, typically a code sent to an email or text after the user enters their account login information. Once the user enters the code, they’ll gain access to the account.
Like all things, MFA is only successful if you use it correctly. Having it enabled on just a few accounts defeats the purpose of implementing it to begin with.
“We’re seeing a breakdown of proper configuration and management of MFA,” says Drew Sanford, Director of Sales Engineering at Continuum. “If you’re managing remote systems or administering user access, you should be using MFA, but you need to be using it for all accounts, especially the MFA systems themselves.” That’s right. Secure the security measures.
“Nothing is worse than protecting your systems with MFA just to find the hacker was able to log in and reset your Google, LastPass, or other accounts,” Drew says
3. Have the Right Resources
There has been a talent gap across the industry for the past few years, and cybersecurity is no different. It’s a job-seeker’s market, with unemployment for cybersecurity professionals close to zero percent. That makes finding talent hard and keeping it even harder. Skilled professionals will demand top dollar for their expertise.
The hiring crunch trickles down to the quality of services. According to research from Continuum, 37% of MSPs say they aren’t able to obtain the right level of in-house cybersecurity skills. Without the right skill sets, your security team might not be able to meet the demands of your customers and leave them vulnerable to a security incident.
When it comes time to start providing security services, if you haven’t started already, you’ll need to decide whether to build your security offerings on your own, buy an established security company, or partner with a security vendor. There are pros and cons to each option, and there is no ‘one-size-fits-all’ approach. Your security requirements are unique to your business, so it’s crucial to pick the strategy that works for you—and getting it right can help you stand out from the competition.
According to Continuum’s white paper, Underserved and Unprepared: The State of SMB Cybersecurity in 2019, cybersecurity is becoming a determining factor for SMBs deciding to use or continue using an MSP. How much so? 84% of SMBs surveyed who do not currently use an MSP would consider using one if they offered the right security services.
4. Protect Your House
This has become one of our more popular cybersecurity calls to action, but it’s not just a saying, it’s an integral part of running your business. When you protect your house, you’re ensuring you have the proper security controls and procedures in place across your organization. Yes, you’ll be more secure, but you’ll also be showing current and potential customers that you’re committed to security.
You build trust with an SMB when you show them you not only take proper security precautions, but the solutions you use internally are the ones you’re selling them. Your security offerings are tried and tested. This could be the thing that separates you from the competition.
5. Take Advantage of the TSP-ISAO
According to the Department of Homeland Security, threat actors are exploiting the trusted relationship between technology solution providers (TSPs) and their customers to creep unnoticed into customers’ networks. In October 2019, ConnectWise announced the creation of the Technology Solution Provider Information Sharing and Analysis Organization (TSP-ISAO).
The TSP-ISAO is an independent organization formed to provide a secure infrastructure within the TSP industry to set the standard for TSPs in the services and products they provide to their clients, as well as the people, processes, and tools they employ.
“We believe that the TSP-ISAO has an important role to play in educating MSPs and SMBs to the existential nature of the threats they face. Both MSP and SMB industries have never faced a threat like this and are collectively unprepared to understand the true nature of the threat. Working with our public and private partners, we will develop programming to ensure the threat is understood and countered,” said TSP-ISAO Executive Director, MJ Shoer.
This article was provided by our service partner : connectwise.com