Ransomware Variants an MSP Should Watch Out For
We can all agree that ransomware is one of the biggest and most destructive threats managed service providers and their clients have faced in recent years. Currently, there are well over 120 separate ransomware families, and there’s been a 3,500% increase in cyber criminal internet infrastructure for launching attacks since the beginning of 2016. And nearly 90% of MSP report their clients have been hit by ransomware in the last year. But, in spite of these numbers, nearly 70% of MSP still aren’t completely confident their clients’ endpoints are secure against these insidious attacks.
Know Your Enemy
In addition to maintaining up-to-date endpoint security that uses real-time analysis to detect zero-day attacks, it’s important to know your enemy. Cybersecurity provider Webroot recently put together a list of the top 10 nastiest ransomware variants of 2017. You’ve probably heard of the big, newsworthy names that made the list, like WannaCry, NotPetya, and Locky, but here’s a few more MSPs should watch out for.
- CrySis
CrySis attacks by compromising Remote Desktop Protocol (RDP). RDP is a common method for deploying ransomware because criminals can get into admin accounts that have access to an entire organization. First detected in February 2016, CrySis took some time to spread, and really came into its own in 2017. - Nemucod
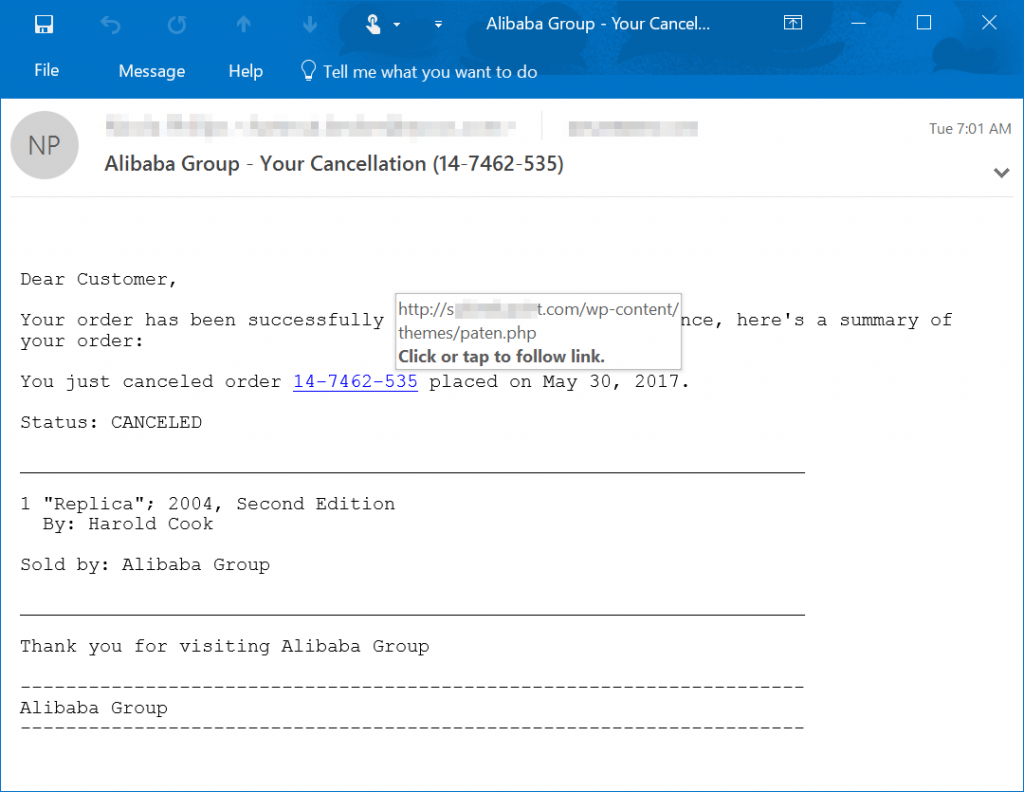
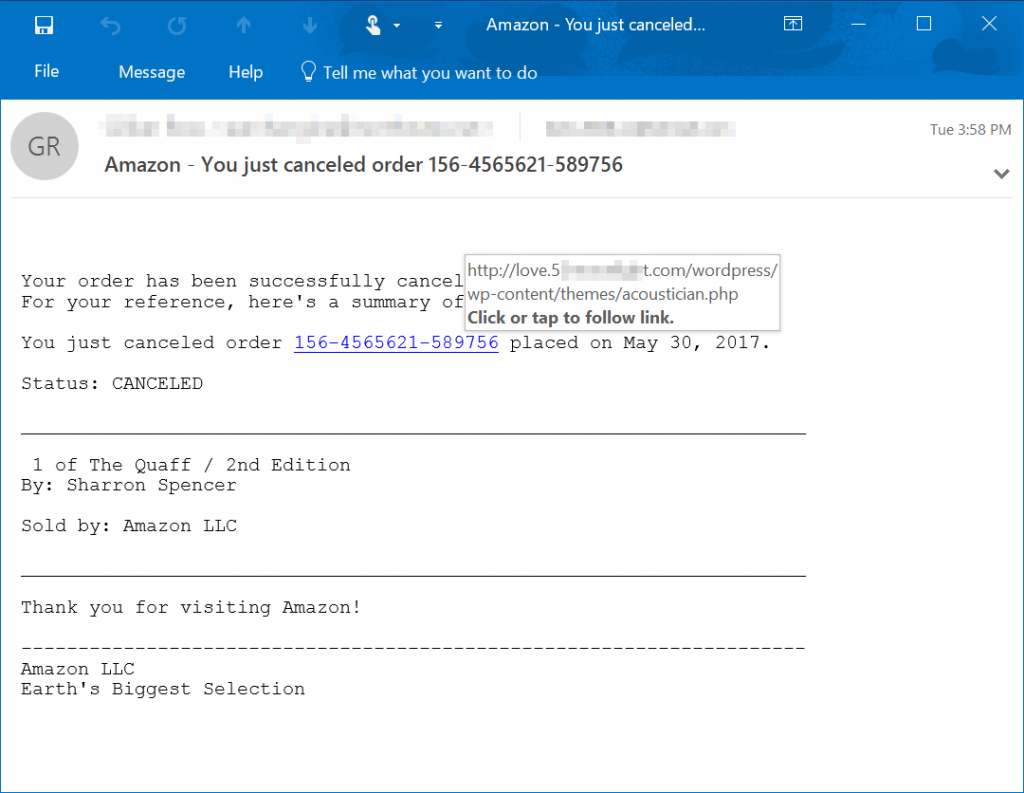
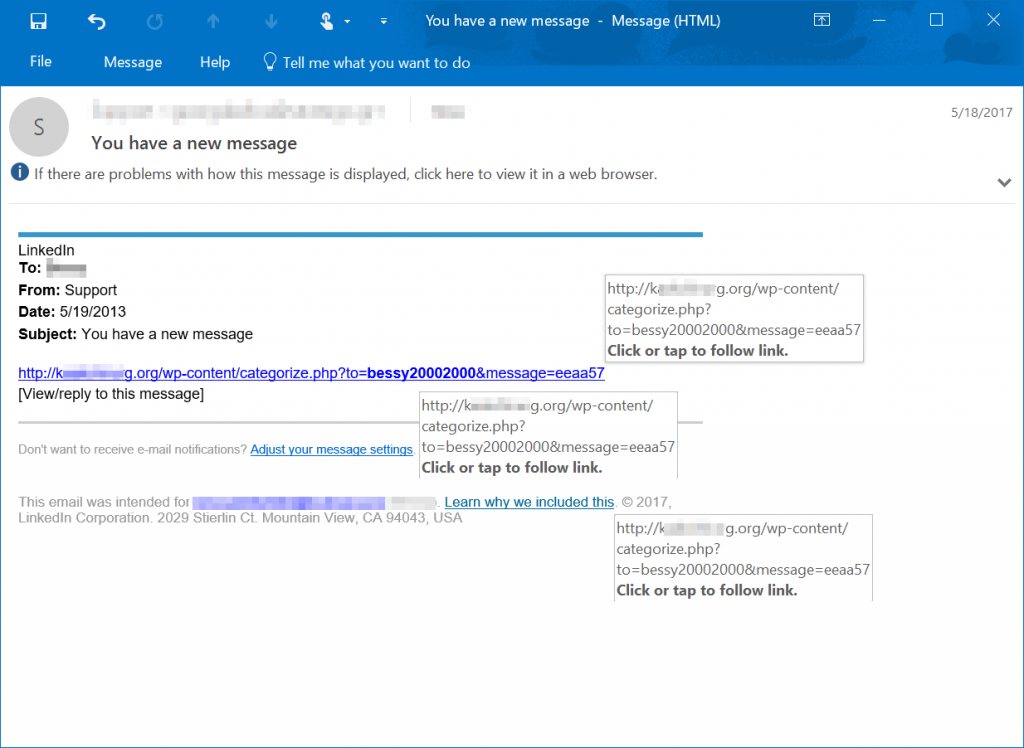
This ransomware variant arrives via phishing emails disguised as a shipping invoice. Nemucod downloads malware and encryption components stored from hacked websites, and would have most likely been the worst of the phishing email attacks for the year, had Locky not resurfaced in August. - Jaff
Like Nemucod and Locky, Jaff uses phishing emails to spread. It also uses similar techniques to other successful ransomware attacks, including Dridex. - Spora
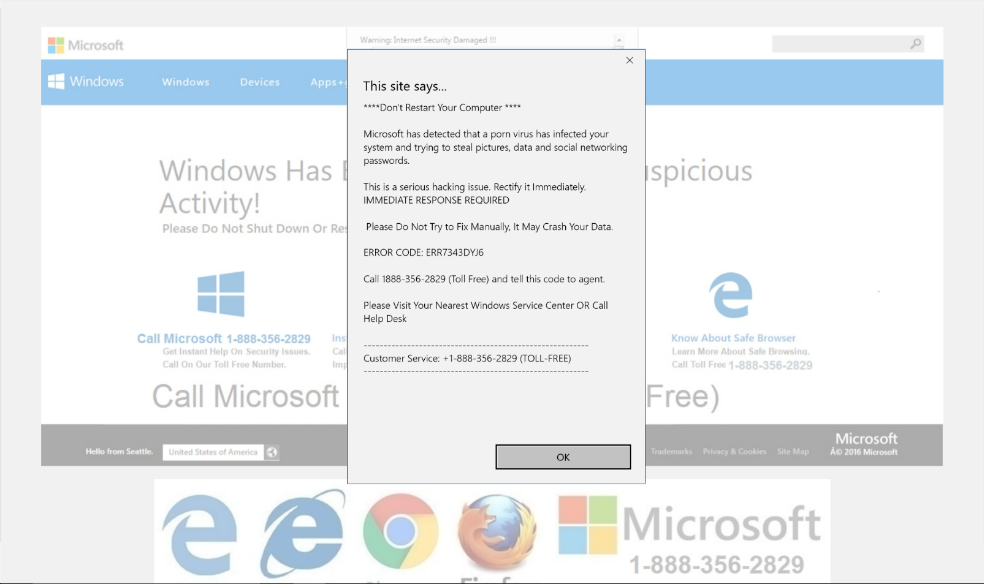
This ransomware is distributed by legitimate websites that have been compromised with malicious JavaScript code. The sites display a pop-up prompt to visitors, instructing them to update their Chrome browsers to continue viewing the page. But when the unsuspecting user downloads the “Chrome Font Pack”, they get the infection instead. - Cerber
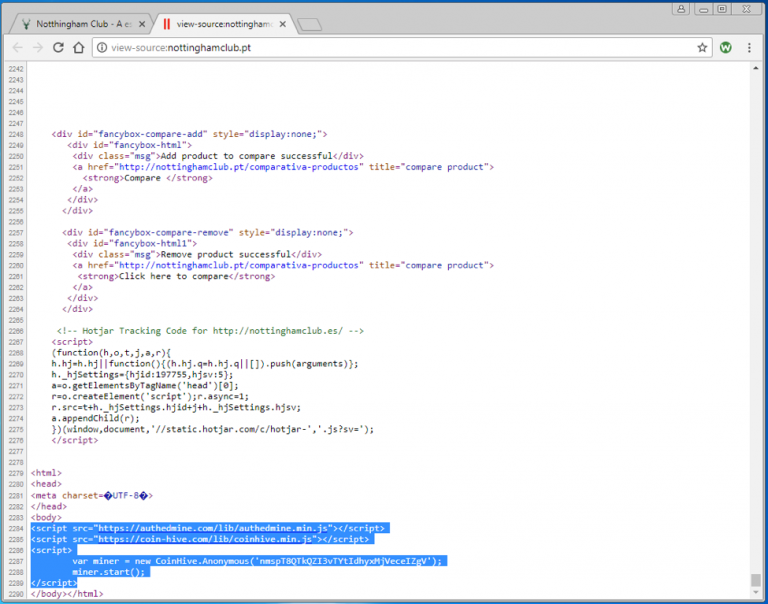
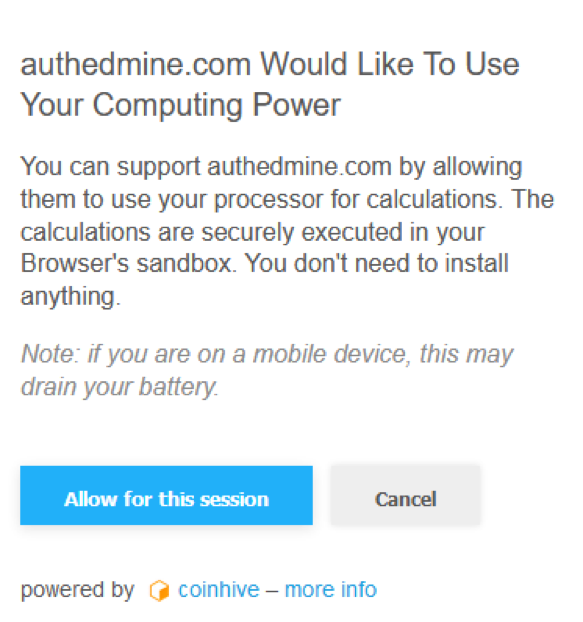
Cerber also uses phishing and RDP, but unlike some of its colleagues, it distributes ransomware-as-a-service (RaaS). This “service” allows aspiring cybercriminals to use pre-packaged ransomware tools as they choose, while the Cerber author gets a 30% cut of any profits made.
Keeping Your Clients Safe
There are a number of steps an MSP can take to keep clients safe.
- First, educate your clients. Be sure to teach them how to spot suspicious emails and how to check legitimacy any time an email seems a little off. We also recommend implementing an end user cybersecurity training program.
- Second, keep applications and plugins up to date, and make sure your clients are using reliable cloud-based antimalware, web filtering, and firewalls.
- Third, use your operating system to your advantage. Set up Windows® OS policy restrictions, disable auto-run, disable VBS, and filter executables from emails.
- Fourth, ensure your clients run regular backups, set up offline air gap backups with multiple copies of each file, and maintain up-to-date business continuity measures.
This article was provided by our service partners Webroot & Connectwise.