Posts
Is Your Organization Ready to Defend Against Ransomware Attacks?
Without question, cybercrime is escalating and ransomware attacks and threats abound. Learn how to defend against ransomware, how infection can occur and how you can fight back.
Cybercrime is reaching unprecedented heights. And with the recent “WannaCry” ransomware attack, cyberthreats are back at the top of every IT department’s list of priorities and concerns. Unfortunately, it’s a trend that is unlikely to be curbed anytime soon. Cybersecurity communities have estimated that the total cost of cybercrime damage worldwide is estimated at $6 Trillion annually by the end of 2021, forcing more and more businesses to invest in cybersecurity spending on products and services to protect their business critical data from potential ransomware attacks.
Here I’ll talk more about what ransomware is, how infections can occur and how your business can be more prepared to defend against potential attacks.
What is ransomware?
Ransomware is typically defined as a subset of malware where the data on a victim’s computer becomes inaccessible and payment is demanded (usually in the form of bitcoin or other cryptocurrencies), before the data is decrypted and the victim can re-access their files.
Ransomware attacks can present themselves in a variety of forms but Microsoft Malware Protection Center explains that the two most widespread ransomware families to be reported in 2016/17 were:
- Lock-screen ransomware
- Encryption ransomware
Typically, lock-screen ransomware will present victims with a full-screen message which then prohibits the user from accessing their PC or files, until a payment is made. Whereas encryption ransomware will modify the data files via encryption methods so that the victim cannot open them again. In both cases, the attackers are in total control and demand large sums of money to access or unlock the files.
How does a ransomware infection occur?
On average, most ransomware infections occur through email messages carrying Trojans that attempt to install ransomware when opened by victims, or alternatively, websites that attempt to exploit vulnerabilities in the victim’s browser before infecting the system with ransomware.
Multiple high-profile incidents in 2016/17 alone, have demonstrated the destruction ransomware attacks can have on enterprise networks just as easily as on individual PCs. For example, EternalBlue (a Windows exploit) released by the mysterious hacking group Shadow Brokers in April 2017 breached spy tools at the National Security Agency (NSA) and offered stolen data for auction, and the WannaCry strain targeted thousands of targets including the National Health Service in the UK (in total netting ~52 bitcoins or around $130,000 worth of ransom).
Not to mention many other widespread strains of ransomware including Petya, Nyetya, Goldeneye, Vault 7, Macron which have had devastating effects on countries, enterprises, election debates and individuals around the world. Attacking enterprise networks in this manner, is even becoming even more attractive because of the value of the files and data that large enterprises own means attackers can demand higher monetary values for ransom.
How to fight back
The increasing threats of ransomware attack should come as no surprise, because in reality organizations have always been under threat from malicious cyberattacks, viruses and ransomware, just more so now than ever before, and IT managers should continually be looking for ways to better protect their valuable data. Therefore, it is essential that your organization has a plan in place to defend against such attacks, minimize financial impact, reduce IT impact and maintain brand reputation.
The industry recognized recommendations suggest organizations follow the simple 3-2-1 rule and the implementation of a strong security plan. The goal of the 3-2-1 rule is to provide customers with a data protection solution that maximizes application uptime, and data availability in the event of a disaster striking.
With the proper execution of the 3-2-1 backup principles, IT managers can protect their data by:
- Maintaining 3 copies of data (primary data and two copies)
- Store backup copies on 2 different media types (such as tape, disk, secondary storage or cloud)
- Keep 1 copy off-site (either on tape or in the cloud, since disasters can strike without notice, if all other forms of protection fail, you still have access to offline data!)
Now available: Windows Server 2016 Security Guide!
Windows Server 2016 includes major security innovations that can help protect privileged identity, make it harder for attackers to breach your servers, and detect attacks so that you can respond faster. This is powerful technology, and all that’s missing is guidance on how to best deploy and use Windows Server 2016 to protect your server workloads.
Microsoft have recently released their Windows Server 2016 Security Guide.
This paper includes general guidance for helping secure servers in your environment as well as specific pointers on how you can utilize new security features in Windows Server 2016. We are committed to continue our effort to provide you with the right security solutions so that you can better protect, detect and respond to threats in your datacenter and private cloud.
Application Whitelisting Using Software Restriction Policies
Software Restriction Policies (SRP) allows administrators to manage what applications are permitted to run on Microsoft Windows. SRP is a Windows feature that can be configured as a local computer policy or as a domain policy through Group Policy with Windows Server 2003 domains and above. The use of SRP as a white-listing technique will increase the security feature of the domain by preventing malicious programs from running since the administrators can manage which software or applications are allowed to run on client PCs.
Blacklisting is a reactive technique that does not extend well to the increasing number and variety of malware. There have been many attacks that cannot be blocked by the blacklisting techniques since it uses undiscovered vulnerabilities known as zero-day vulnerabilities.
On the other hand, Application white-listing is a practical technique where only a limited number of programs are allowed to run and the rest of the programs are blocked by default. It makes it hard for attackers to get in to the network since it needs to exploit one of the allowed programs on the user’s computer or get around the white-listing mechanism to make a successful attack. This approach should not be seen as replacement standard security software such as anti virus or firewalls – it is best used in conjunction with these.
Since Microsoft Windows operating systems have SRP functionality built in, administrators can readily configure an application white-listing solution that only allows specific executable files to be run. Service Restriction Policies can also restrict which application libraries are permitted to be used by executable’s.
There are certain recommended SRP settings by NSA Information Assurance Directorate’s (IAD) Systems and Network Analysis Center (SNAC). It is advised to test any configuration changes on a test network or on a small set of test computers to make sure that the settings are correct before implementing the change on the whole domain.
There is known issues on certain Windows versions to consider: for example minor usability issue such as when double-clicking a document, it may not open the associated document viewer application, another is the software update method that allows users to manually apply patches may not function well once SRP is enforced. We may see these issues addressed with a hotfix provided by Microsoft. Automatic updates are not affected by SRP white-listing and will still function correctly. SRP settings should be tested thoroughly due to issues like this to prevent causing a widespread problem in your production environment.
The use of path-based SRP rules are recommended since it has shown unnoticeable performance impact on host after a good deal of testing. Other rules may provide greater security benefits than path-based rules but it has an increased impact on host performance. Other rules like file hash rules are more difficult to manage and needs constant updates each time any files are installed or updated, another is the certificate rules which is somehow limited since not all the applications’ files are digitally signed by their software publishers.
There are certain steps to follow in implementing SRP in Active Directory domain which can be done through the steps below:
1. Review the domain to find out which applications are operating on domain computers.
2. Configure SRP to work in white-listing approach.
3. Choose which applications must be permitted to run and make extra SRP rules as required.
4. Test the SRP rules and form additional rules as needed.
5. Install SRP to sequentially larger Organizational Units until SRP is functional to the entire network.
6. Observe SRP continuously and adjust the rules when needed.
SRP configuration as described above can drastically increase security stance of a domain while continuously letting users to run the applications they need to remain productive for their work.
Security Awareness: A Tale of Two Challenges
SANS Institute has recently releases their findings from a survey ‘Securing The Human 2016’ about Security Awareness that led them to uncover two key findings: First, the security awareness team are not getting enough support they need and second, the experts in the field of security awareness lack soft skills to get the knowledge they have distributed properly.
This is the second annual security awareness report released and its main goal is to allow security awareness officers to make knowledgeable decisions on how to make their security programs better and to let them compare their organizations program to other programs in their industry.
SANS Institute provides information security training all over the world. For over 25 years of experience they are considered as the most trusted and the principal source of information security training. SANS : Securing The Human is an institute division that gives complete and comprehensive security awareness solution to organizations which can help them to effectively manage their human cyber security risk.
Report Summary
This years’ approach tells a story through data, compared to last year where the data and results were presented in the order the survey was taken. The data tells a story about the tale of two challenges which they began to see as they worked through the data.
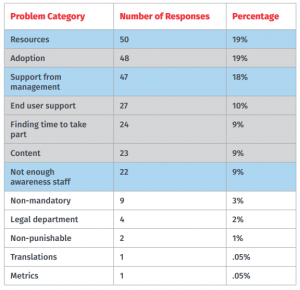
They conducted a survey on what are the biggest challenges that security officers encountered and the results were tremendous giving them over a 100 different topics. The responses were categorized into 12 categories by Ingolf Becker, from University College of London. The seven problem categories include: resources, adoption, support from management, end user support, finding time to take part, content and not enough staff awareness. They have focused on the first seven on the list which fell into two general groups: lack of resources, time, support and/or not having an impact. The people are either limited on their ability to execute (46%) and/or fails to deliver the needed impact (47%). This starts the tale of two challenges and this report is focused on understanding these challenges and identifying possible solutions.
Categorization of Biggest Challenge Awareness Programs Face
Similar to last year’s report, the data showed that a lot of awareness staff has insufficient resources, time and support to get the work completed.
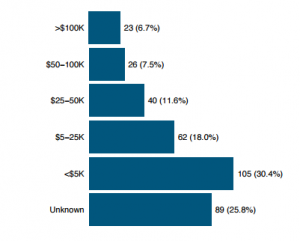
Resources, as defined by Ingolf, are about the shortage of money or technical resources. Budget wise more than 50% of respondents stated that they either have a budget of $5,000 or less or they are not aware if they do have a budget and only 25% reported a budget of $25,000 or more.
Estimated Budget for 2016
Less than 15% of the respondents work full-time in awareness which is an improvement from last year’s 10% it is still considerably low. While there is an improvement only 65% says that they only spend 25% or less of their time on awareness.
Even if the people are getting support for security awareness they do not have or there is only a few metrics considered that demonstrates the human problem, impact or awareness. Most are focused on phishing which is a common top human risk, which is good but this is only one of the many organizational human risk to deal with.
Communication was identified to be the number one blocker in the program. This is more evident in larger organizations where they have 1,000 employees or more. Highly technical people reports to the highly technical department have communications as their biggest blocker even if their main job is to communicate to the organization.
Recommendations
As a recommendation they proposed that communications as one of the most critical soft skills needs to be addressed by training; place someone from the communications department into the awareness team or hire someone with the soft skills they need. As for the engagement, people needs to know why they should care about security awareness and target them at an emotional level rather than giving them statistics and numbers.
A note on Group Policy and gpudate
When I first started learning about Active Directory, Group Policy always seemed very fickle. Sometimes I could run GPUpdate, other times I had to append the /force option.
As it turned out, Group Policy was always working – I just didn’t understand it. So what’s the difference between GPUpdate and GPUpdate /force? Well –
GPUpdate: Applies any policies that is new or modified
GPUpdate /force: Reapplies every policy, new and old.
So which one should I use? 99% of the time, you should only run gpupdate. If you just edited a GPO and want to see results immediately, running gpupdate will do the trick. In fact, running GPUpdate /force on a large number of computers could adversely affect network resources. This is because these machines will hit a domain controller and reevaluate every GPO applicable to them.
Notice the Group Policy Update option for OUs:
What is Private Cloud Hosting?
A private cloud is a model of cloud computing in which a partitioned and secure cloud based environment is provided for individual clients. As with any other cloud model, private clouds provide computing power as a service within a visualized environment using an pool of physical computing resource. However, the private cloud model, this computing power is only accessible by a single organisation providing which offers greater control and privacy.
Public and private cloud deployment models differ even with cost where you can Compare Price of Google vs Amazon Cloud & Dedicated Servers. Public clouds, such as those from Amazon Web Services or Google Compute Engine, share a computing infrastructure across different users, business units or businesses. However, these shared computing environments aren’t suitable for all businesses, such as those with mission-critical workloads, security concerns, uptime requirements or management demands. Instead, these businesses can provision a portion of their existing data center as an on-premises — or private — cloud.
A private cloud provides the same basic benefits as that of a public cloud. These include self-service and scalability; multi-tenancy; the ability to provision machines; changing computing resources on-demand; and creating multiple machines for complex computing jobs and business units pay only for the resources they use.
In addition, private cloud from Computers in the City offers hosted services to a limited number of people behind a firewall, so it minimizes the security concerns some organizations have around the cloud. Private cloud also gives companies direct control over their data.
Windows 10 – To Upgrade or Not to Upgrade
Since last year, we’ve been telling our clients to hold off on upgrading. We even used Group Policy and our Management Agents to disable the upgrade patch. It’s been a long and treacherous journey, but we finally believe Windows 10 is ready for Prime Time. We’ve even seen it increase performance in some older machines. We are now recommending our clients to upgrade to Windows 10 to take advantage of the free licensing and extended support for the OS. With all the major bugs fixed, we’re confident you will find it to be stable and useful. Applications are also compatible more often than not. In fact, all of NetCal’s employees are now on Windows 10. We did all the testing so our clients don’t have to worry.
Contact us so we can evaluate your environment.
Q: If I upgrade, can I use Windows 7/8/8.1 again?
A: You can always reinstall using existing media or downgrade using the built-in Windows 10 recovery process (only works for 1 month after upgrade).
Q: What if I don’t upgrade in time? How much would a Windows 10 license cost then?
A: Although Microsoft has been rather vague thus far, the general consensus would be that the license would cost $120 for Win10Home and $200 for Win10Pro.
Q: How would I upgrade after the expiration date?
A: For those that fail to upgrade in time or simply chose not to, Windows 10 can be purchased via the Microsoft Store or through Retail Partners.
Q: If I need to reinstall Windows 10, what key can I use?
A: All Windows 7 and Windows 8/8.1 keys will work with the latest Windows 10 installation media.
Q: If I upgrade, will I be charged a subscription service fee after that?
A: According to Microsoft, if you upgrade before July 29th, Windows 10 will continue to be free and supported for the rest of the life of the device. This is also similar to how your OEM Windows licenses work.
Another layer of protection: Cryptolocker and other malware
Preventative Workstation protection:
This virus launches from a specific location on the workstation, thus it’s recommended to add a group policy setting to block it from Windows Vista/7/8 and from XP.
Use software restriction policies as follows:
Windows 7:
You can use Software Restriction Policies to block executables from running when they are located in the %AppData% folder, or any other folder. File paths of the infection are: C:\Users\User\AppData\Roaming\{213D7F33-4942-1C20-3D56=8-1A0B31CDFFF3}.exe (Vista/7/8)
Support Services
Cloud Services
Other
Bay Area
2005 De La Cruz Blvd.Ste 204
Santa Clara, CA 95050
408–228–4488
Greater Los Angeles
626–768–7799