A Miner Decline: The Surprising Slowdown of Cryptomining
In Webroot’s 2018 mid-term threat report, we outlined how cryptomining, and particularly cryptojacking, had become popular criminal tactics over the first six months of last year. This relatively novel method of cybercrime gained favour for being less resource-intensive and overtly criminal when compared to tactics involving ransomware. But mining cases and instances of mining malware seem to have dropped off significantly in the six months since this report, both anecdotally and in terms of calls to our support queue.
The crytpo world has gone through significant turmoil in this time, so it’s possible the reduced use of malicious cryptojacking scripts is the result of tanking cryptocurrency values. It’s also possible users are benefitting from heightened awareness of the threat and taking measures to prevent their use, such as browser extensions purpose-built to stop these scripts from running.
Setting aside the question of why for a moment, let’s take a look at some stats illustrating that decline during that time period.
Cryptojacking URLs seen by Webroot over six months beginning 1 July through 31 December, 2018, Webroot SecureAnywhere client data.
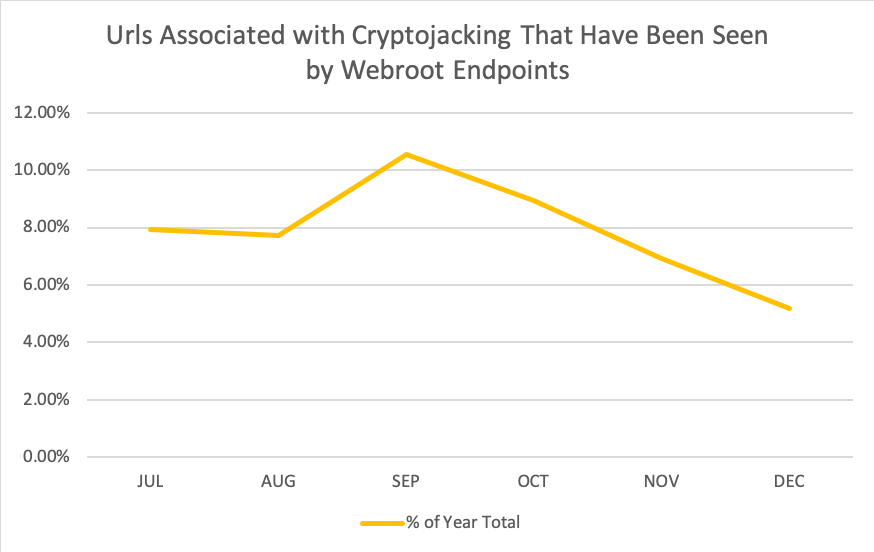
Webroot endpoints detected URLs associated with over 17,000 cryptojacking instances over the last year.
New miner malware seen by Webroot
Data from six months beginning 12 July through 9 Jan, 2019, Webroot data, units logarithmic.
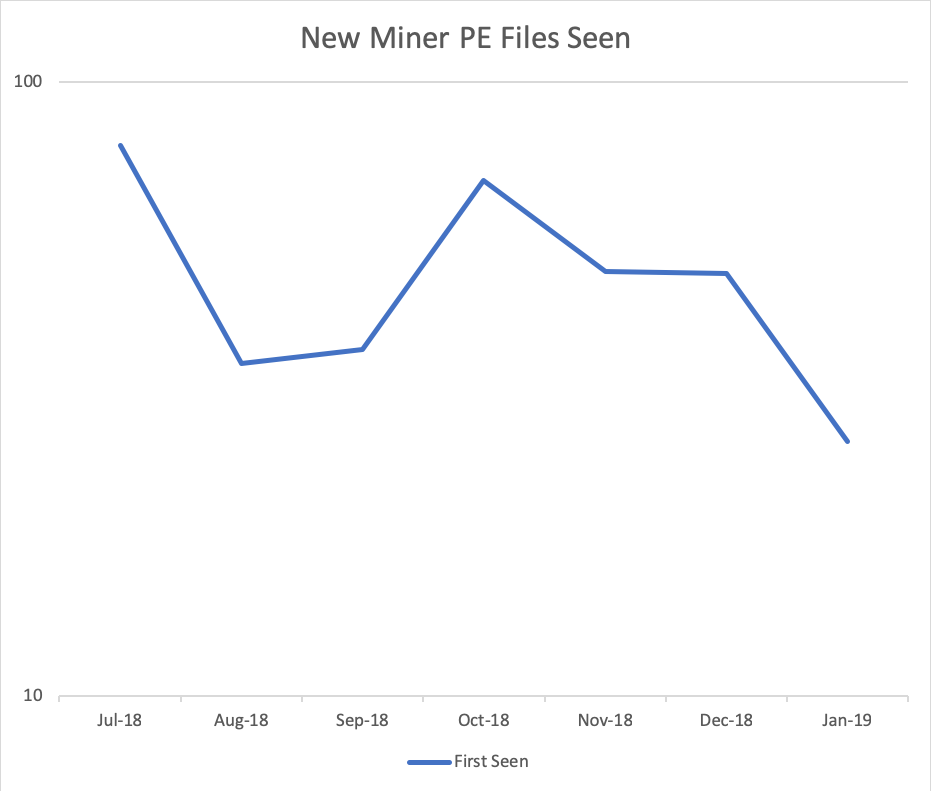
Portable executable mining malware seen by Webroot threat intelligence. Data from hundreds of millions of Webroot sensors.
Monero mining profitability ($)
Data covering six months from 12 July – 9 Jan, 2019, Bit Info Charts, units logarithmic
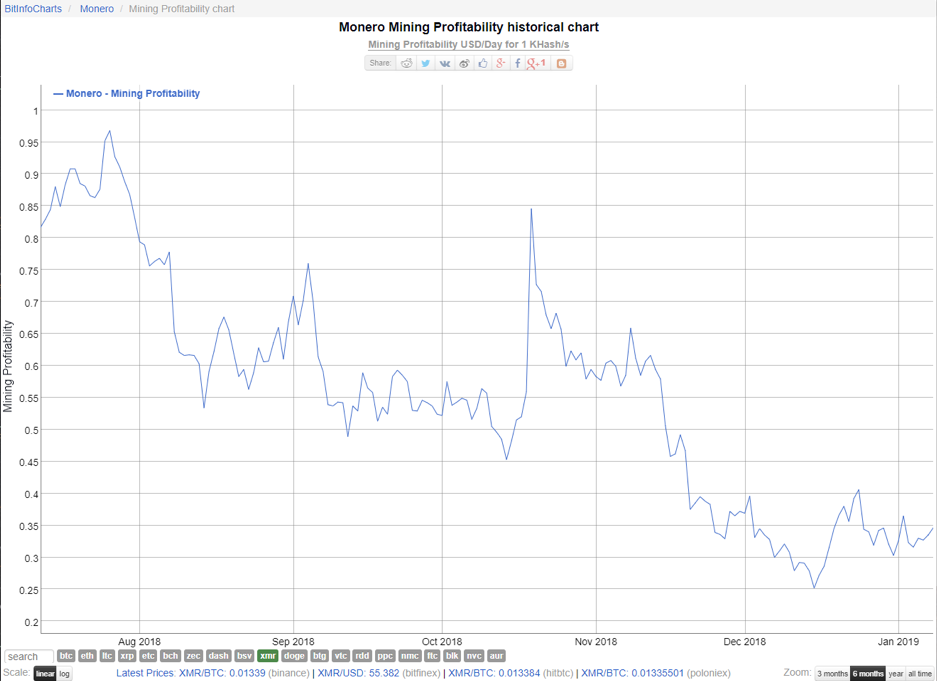
We chose Monero as the currency to analyse here because of its popularityamong crooks operating miners or cryptojacking sites. However, results for Bitcoin over the same time period are similar.
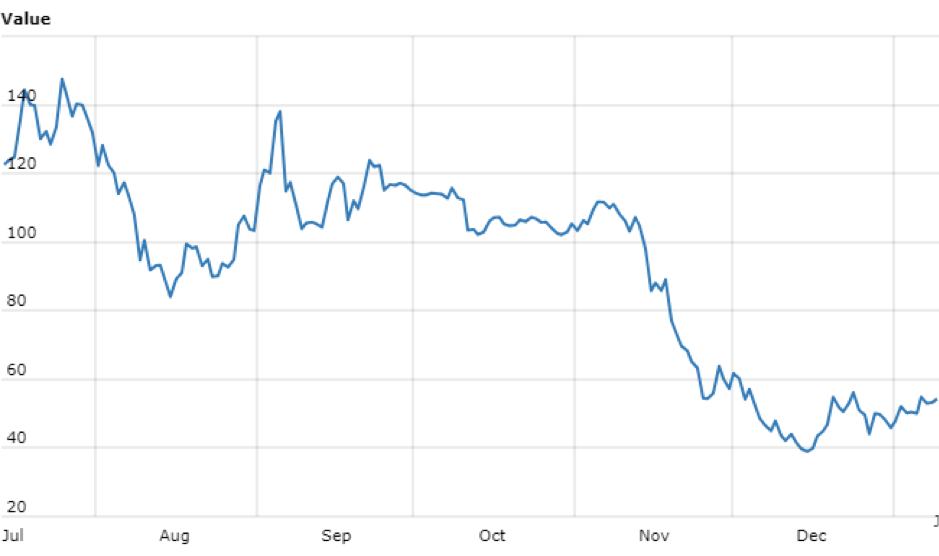
Monero price ($)
Data covering six months from 12 July through 9 Jan, 2019, World Coin Index
Interpreting the data
None of the graphs are identical, but without too much statistical comparison, I think a broad trend can be seen: malicious mining is on the decline alongside a general decline in coin value and coin mining profitability.
Profitability affecting criminal tactics is of course not surprising. The flexibility of exploit kits and modern malware campaigns like Emotet mean that cybercriminals can change tactics and payloads quickly when they feel their malware isn’t netting as much as it should.
Thanks to the dark web, criminal code has never been easier to buy or rent than in recent years, and cryptocurrencies themselves make it easy to swap infection tactics while keeping the cash flowing. Buying or renting malicious code and malware delivery services online is easy, so the next time the threat landscape changes, expect criminals to quickly change with it.
Should I still care about miners?
Yes, absolutely.
Cryptocurrency, cryptomining, and malicious cryptomining aren’t disappearing. Even with this dip, 2018 was definitely a year of overall cryptocrime growth. Our advanced malware removals teams often spot miner malware on machines infected by other malware, and it can be an indication of security holes in need of patching. And any illegal mining is still capable of constantly driving up power bills and frustrating users.
Where are cybercriminals focused now?
Information theftis the current criminal undertaking of choice, a scary development with potentially long-lasting consequences for its victims that are sometimes unpredictable even to thieves. The theft, trade, and use for extortion of personal data will be the focus of our next report.
What can I do?
Cryptojacking may only be on the decline because defences against them have improved. To up your chances of turning aside this particular threat, consider doing the following:
- Update everything. Even routers can be affected by cryptojacking, so patch/update everything you can.
- Is your browser using up lots of processor? Even after a reset/reinstall? This could be a sign of cryptojacking.
- Are you seeing weird spikes in your processor? You may want to scan for miner infections.
- Don’t ignore repeated miner detections. Get onto your antivirus’ support team for assistance. This could be only the tip of the iceberg.
- Secure your RDP.
What can Webroot do?
Webroot SecureAnywhere®antivirus products detect and remove miner infections, and the web threat shield blocks malicious cryptojacking sites from springing their code on home office users. For businesses, however, the single best way to stop cryptojacking, is with DNS-level protection. DNS is particularly good at blocking cryptojacking services, no matter how many sites they try to hide behind.
Persistent mining detections might point to other security issues, such as out-of-date software or advanced persistence methods, that will need extra work to fix. Webroot’s support is quick and easy to reach.
In the end, cryptomining and cryptojacking aren’t making the same stir in the cybersecurity community they were some months ago. But they’ve far from disappeared. More users than ever are aware of the threat they pose, and developers are reacting. Fluctuations in cryptocurrency value have perhaps aided the decline, but as long as these currencies have any value cryprojackers will be worth the limited effort they require from criminals.
Watch for the use of cryptominers to be closely related to the value of various cryptocurrencies and remain on the lookout for suspicious or inexplicable CPU usage, as these may be signs that you’re being targeted by these threats.
This article was provided by our service partner : Webroot