EternalBlue reaching new heights since WannaCryptor outbreak
Attack attempts involving the exploit are in hundreds of thousands daily
It has been two years since EternalBlue opened the door to one of the nastiest ransomware outbreaks in history, known as WannaCryptor (or WannaCry). Since the now-infamous malware incident, attempts to use the exploit have only been growing in prevalence. Currently it is at the peak of its popularity, with users bombarded with hundreds of thousands of attacks every day.
The EternalBlue exploit was allegedly stolen from the National Security Agency (NSA) in 2016 and leaked online on April 14, 2017 by a group known as Shadow Brokers. The exploit targets a vulnerability in Microsoft’s implementation of the Server Message Block (SMB) protocol, via port 445. The flaw had been privately disclosed to and patched by Microsoft even before the WannaCryptor outbreak in 2017; yet, despite all efforts, vulnerable systems are widespread even to this day.
According to data from Shodan, there are currently almost a million machines in the wild using the obsolete SMB v1 protocol, exposing the port to the public internet. Most of these devices are in the United States, followed by Japan and the Russian Federation.
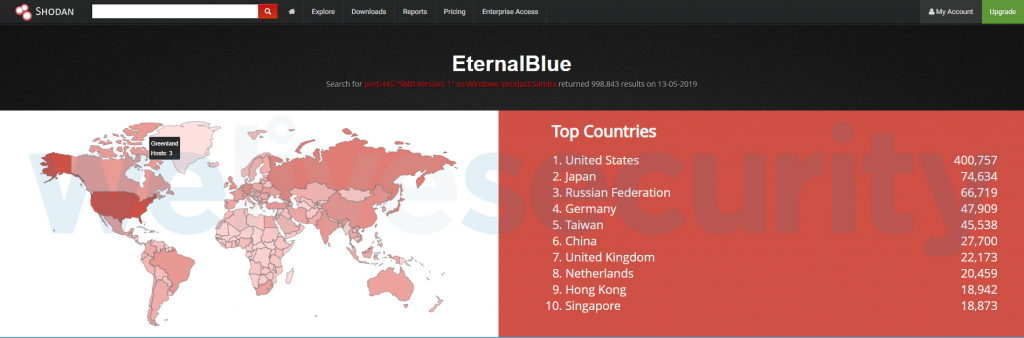
Poor security practices and lack of patching are likely reasons why malicious use of the EternalBlue exploit has been growing continuously since the beginning of 2017, when it was leaked online.
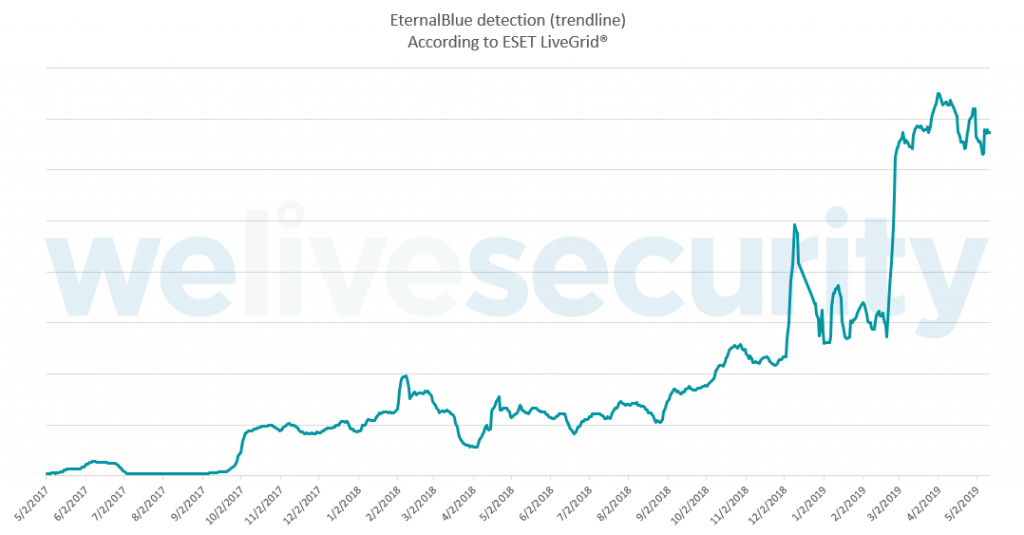
Based on ESET telemetry, attack attempts involving EternalBlue are reaching historical peaks, with hundreds of thousands of instances being blocked every day, as seen in Figure 1.
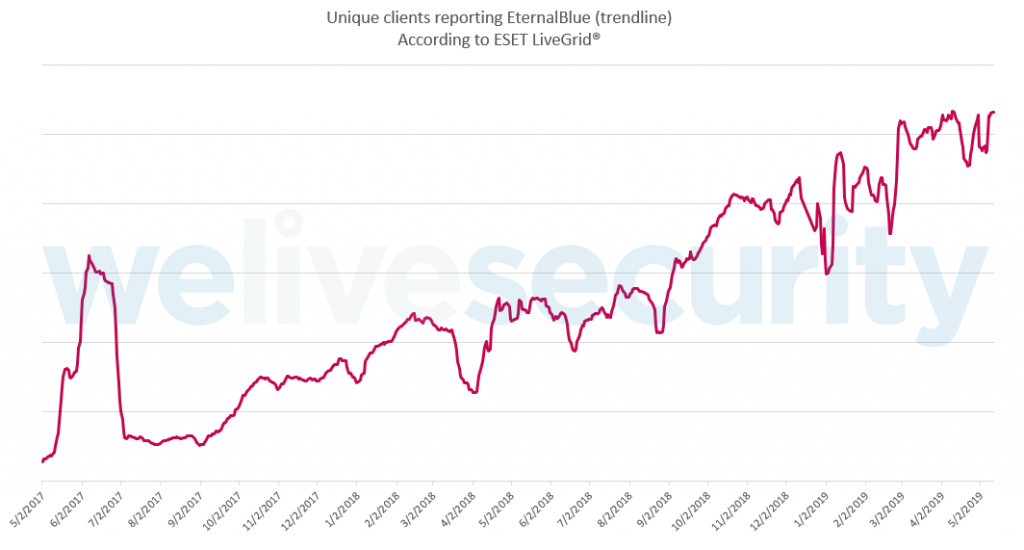
A similar trend can be observed by looking at the number of unique ESET clients reporting thousands of attempts to use the exploit daily, as seen in Figure 2.
Besides malicious use, EternalBlue numbers might also be growing due to its use for internal security purposes. As one of the most prevalent malicious tools, this exploit can be used by company security departments as a means for vulnerability hunting within corporate networks.
EternalBlue has enabled many high-profile cyberattacks. Apart from WannaCryptor, it also powered the destructive Diskcoder.C (aka Petya, NotPetya and ExPetya) campaign and the BadRabbit ransomware campaign in 2017. Well-known cyberespionage actors such as Sednit (aka APT28, Fancy Bear and Sofacy) were also caught using it against hotel Wi-Fi networks.
EternalBlue was also recently seen spreading Trojans and cryptomining malware in China – a return to what the vulnerability was first seen used for, even before the WannaCryptor outbreak – and was advertised by the black hats as the spreading mechanism for a new Ransomware-as-a-Service Yatron.
This exploit and all the cyberattacks it enabled so far highlight the importance of timely patching. Moreover, it emphasizes the need for a reliable and multi-layered security solution that can do more than just stop the malicious payload, such as protect against the underlying mechanism.
This article was provided by our service partner : eset
