The Rise of Information Stealers
As noted in a previous blog post, mining malware is on a decline, partly due to turmoil affecting cryptocurrencies. Ransomware is also on a decline (albeit a slower one). These dips are at least partly the result of the current criminal focus on information theft.
Banking Trojans, hacks, leaks, and data-dealing are huge criminal enterprises. In addition to suffering a breach, companies might now be contravening regulations like GDPR if they didn’t take the proper precautions to secure their data. The ways in which stolen data is being used is seeing constant innovation.
Motivations for data theft
–
Currency
The most obvious way to profit from data theft is by stealing data directly related to money. Examples of malware that accomplishes this could include:
- Banking Trojans. These steal online banking credentials, cryptocurrency private keys, credit card details, etc. Originally for bank theft specialists, this malware group now encompasses all manner of data theft. Current examples include Trickbot, Ursnif, Dridex.
- Point of Sale (POS). These attacks scrape or skim card information from sales terminals and devices.
- Information stealing malware for hijacking other valuables including Steam keys, microtransactional or in-game items
Trade
Data that isn’t instantly lucrative to a thief can be fenced on the dark web and elsewhere. Medical records can be worth ten times more than credit cards on dark web marketplaces. A credit card can be cancelled and changed, but that’s not so easy with identity. Examples of currently traded information include:
- Credit cards. When cards are skimmed or stolen, they’re usually taken by the thousands. It’s easier to sell these on at a reduced cost and leave the actual fraud to other crooks.
- Personal information. It can be used for identity theft or extortion, including credentials, children’s data, social security information, passport details, medical records that can be used to order drugs and for identity theft, and sensitive government (or police) data
Espionage
Classified trade, research, military, and political information are constant targets of hacks and malware, for obvious reasons. The criminal, political, and intelligence worlds sometimes collide in clandestine ways in cybercrime.
As a means of attack
While gold and gemstones are worth money, the codes to a safe or blueprints to a jewellery store are also worth a lot, despite not having much intrinsic value. Similarly, malware can be used to case an organisation and identify weaknesses in its security setup. This is usually the first step in an attack, before the real damage is done by malware or other means.
“In late 2013, an A.T.M. in Kiev started dispensing cash at seemingly random times of day. No one had put in a card or touched a button. Cameras showed that the piles of money had been swept up by customers who appeared lucky to be there at the right moment.” –From a story that appeared in the New York Times
Just another day in the Cobalt/Carbanak Heists
Some examples of “reconnaissance” malware include:
- Carbanak. This was the spear-tip of an attack in an infamous campaign that stole over €1 billion ($1.24 billion) from European banks, particularly in Eastern Europe. The Trojan was emailed to hundreds of bank employees. Once executed, it used keylogging and data theft to learn passwords, personnel details, and bank procedures before the main attacks were carried out, often using remote access tools. ATMs were hacked to spill out cash to waiting gang members and money was transferred to fraudulent accounts.
- Mimikatz, PsExec, and other tools. These tools are freely available and can help admins with legitimate issues like missing product keys or passwords. They can also indicate that a hacker has been on your network snooping. These software capabilities can be baked into other malware.
- Emotet. Probably the most successful botnet malware campaign of the last few years, this modular Trojan steals information to help it spread before dropping other malware. It usually arrives by phishing email before spreading like wildfire through an organisation with stolen/brute-forced credentials and exploits. Once it has delivered its payload (often banking Trojans), it uses stolen email credentials to mail itself to another victim. It’s been exfiltrating the actual contents of millions of emails for unknown purposes, and has been dropping Trickbot recently, but the crew behind the campaign can change the payload depending what’s most profitable.
“Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Emotet continues to be among the most costly and destructive malware affecting state, local, tribal, and territorial (SLTT) governments, and the private and public sectors.”- An August 2018 warning from the American DHS
- Trickbot/Ryuk. Trickbot is a banking Trojan capable of stealing a huge array of data. In addition to banking details and cryptocurrency, it also steals data that enables other attacks, including detailed information about infected devices and networks, saved online account passwords, cookies, and web histories, and login credentials. Trickbot has been seen dropping ransomware like Bitpaymer onto machines, but recently its stolen data is used to test a company’s worth before allowing attackers to deploy remote access tools and Ryuk(ransomware) to encrypt the most valuable information they have. The people behind this Trickbot/Ryuk campaign are only going after big lucrative targets that they know they can cripple.
What are the current trends?
Emotet is hammering the business world and, according to our data, has surged in the last six months of 2018:
Data recorded between 1 July and December 31, 2018. Webroot SecureAnywhere client data.
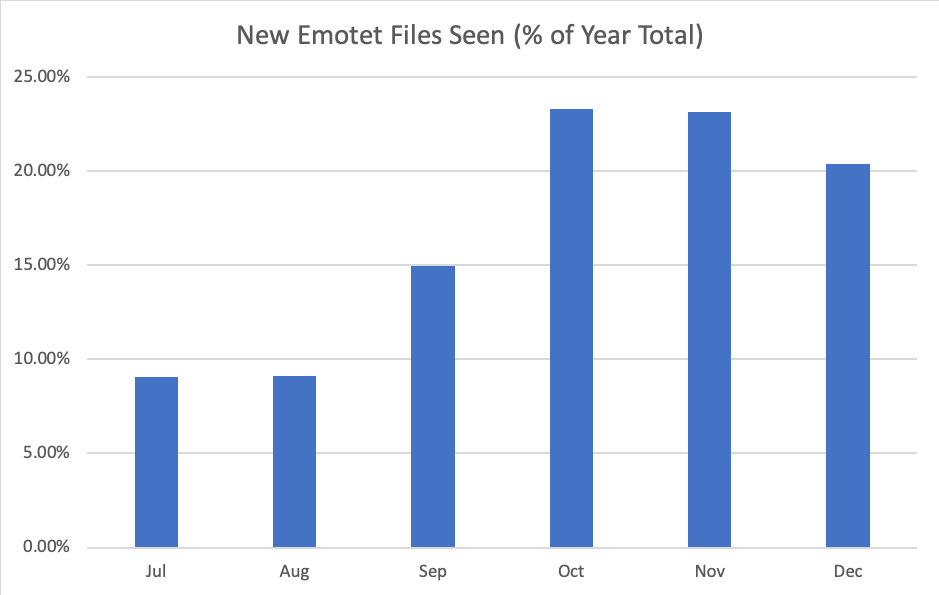
Detection of related malware surged alongside these detections. Almost 20% of Webroot support cases since the start of December have been related to this “family” of infections (Emotet, Dridex, Ursnif, Trickbot, Ryuk, Icedid).
What can I do?
- Update everything! The success of infections such as WannaMine proved that updates to many operating systems still lag years behind. Emotet abuses similar SMB exploits to WannMine, which updates can eliminate.
- Make sure all users, and especially admins, adhere to proper password practices.
- Disable autoruns and admin shares, and limit privileges where possible.
- Don’t keep sensitive information in plain text.
This article was provided by our service partner : Webroot

