Why Firewalls and Antivirus are not enough in our fight for the best network security ?
Understanding Malicious Attacks to Stay One Step Ahead
Network (firewall) and endpoint (antivirus) defenses react to malicious communications and code after attacks have been launched. OpenDNS observes Internet infrastructure before attacks are launched and prevent those malicious internet connections happening in the first first. Learning all the steps of an attack is key to understanding how OpenDNS can bolster your existing defenses.
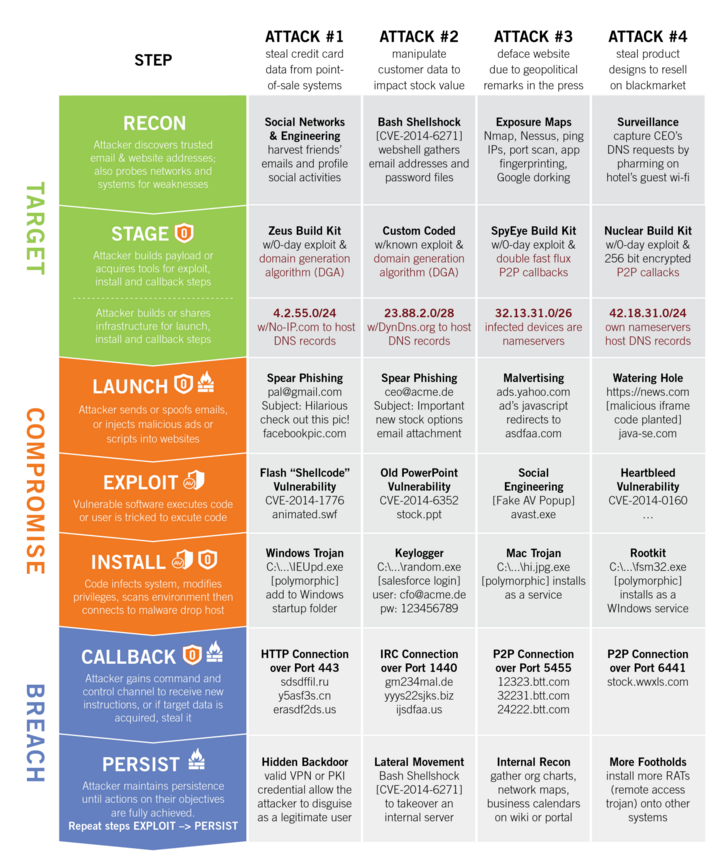
Each step of the attackers operation provides an opportunity for network security providers to find the attack and defend the intrusion.
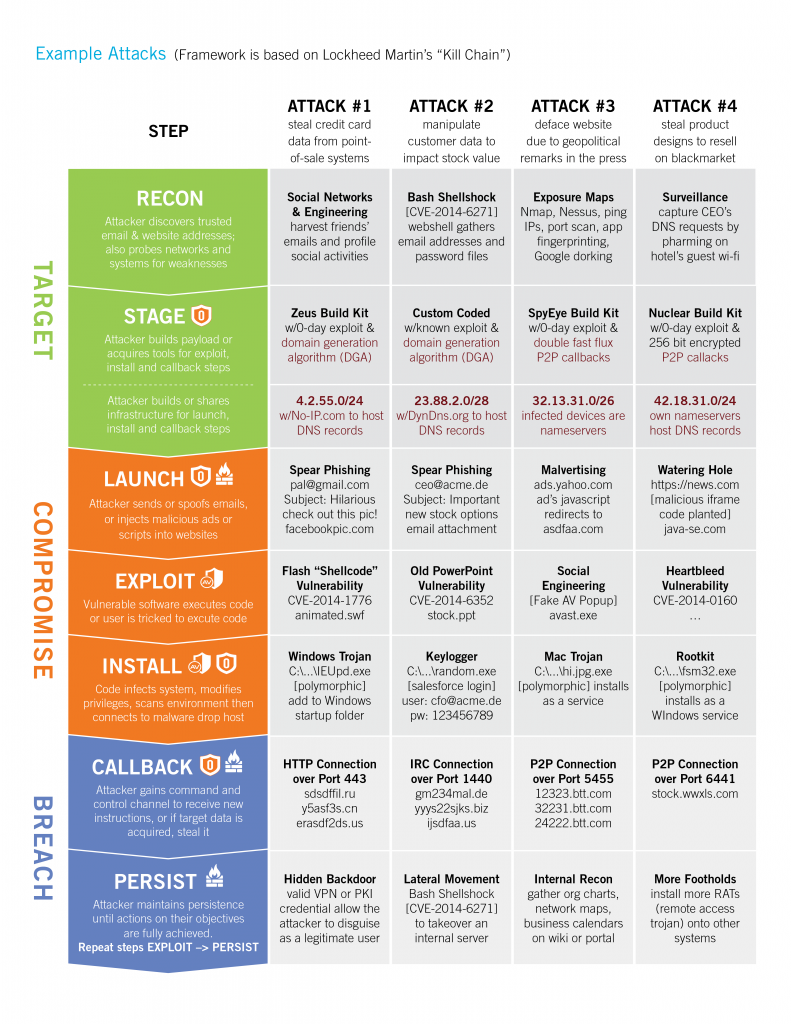
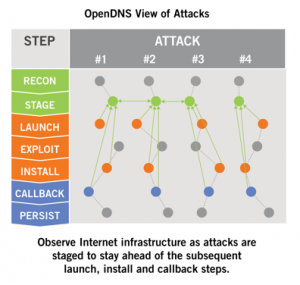
High level summary of how attacks are laid out.
—> RECON: Many reconnaissance activities are used to learn about the attack target
—> STAGE: Multiple kits or custom code is used to build payloads. And multiple networks and systems are staged to host initial payloads, malware drop hosts, and botnet controllers
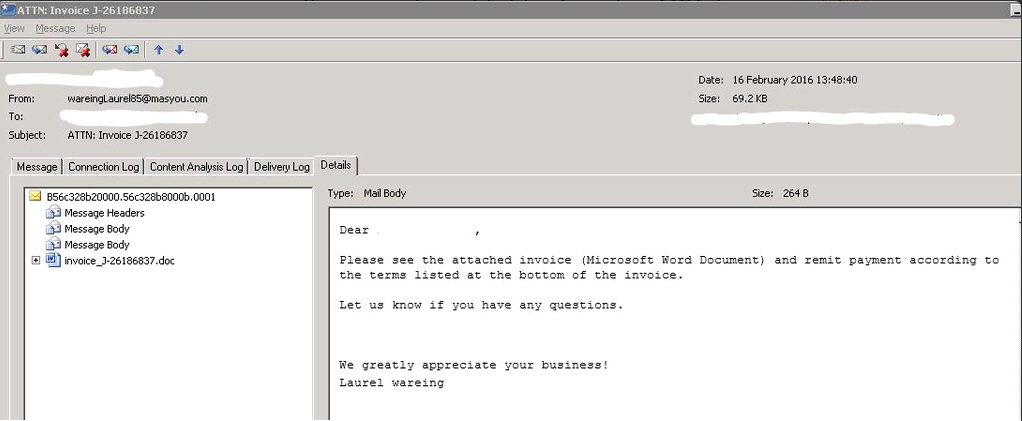
—> LAUNCH: Various Web and email techniques are used to launch the attack
—> EXPLOIT: Both zero-day and known vulnerabilities are exploited or users are tricked
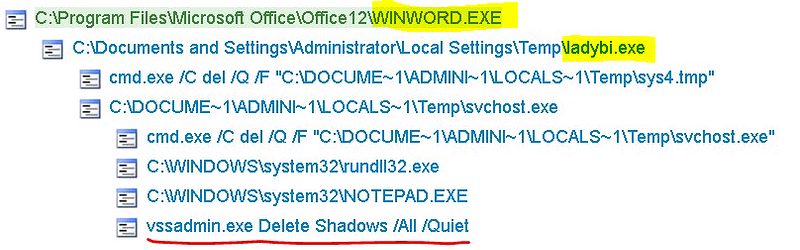
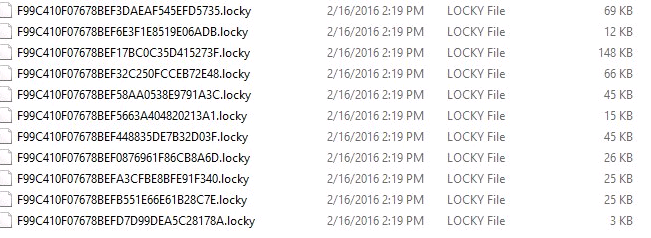
—> INSTALL: Usually the initial payload connects to another host to install specific malware
—> CALLBACK : Nearly every time the compromised system callbacks to a botnet server
—> PERSIST : Finally, a variety of techniques are used to repeat through steps 4 to 7
We do not have to understand each tool and technique that attackers develop. The takeaway from this is to simply understand how multiple and often repeated, steps are necessary for attackers to achieve their objectives undermining your existing network security tools.
Compromises happen in seconds. Breaches start minutes later and can continue undetected for months. Operating in a state of continuous compromise may be normal for many. but no one should accept a state of persistent breach.
Existing defenses cannot block all attacks.
Firewalls and AntiVirus stop many attacks during several steps of the ‘kill chain’, but the volume and velocity of new attack tools and techniques enable some to go undetected for minutes or even months.
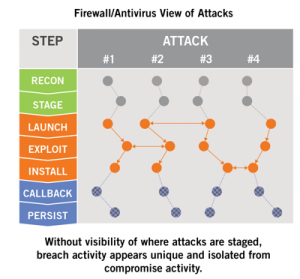
Firewalls know whether the IP of a network connection matches a blacklist or reputation feed. Yet, providers must wait until an attack is launched before collecting and analyzing a copy of the traffic. Then, the provider will gain intelligence of the infrastructure used.
Antivirus solutions know whether the hash of the payload match a signature database or heuristic. Yet providers must wait until a system is exploited before collecting and and analyzing a sample of the code before gaining intelligence about the payload used.
The OpenDNS Solution
Stop 50 to 98 percent more attacks than firewalls and antivirus alone by pointing your DNS traffic to OpenDNS.
OpenDNS does not wait until after attacks launch, malware install, or infected systems callback to learn how to defend against attack. By analyzing a cross-section of the world’s Internet activity, OpenDNS continuously observe new relationships forming between domain names, IP addresses, and autonomous system numbers (ASNs). This visibility enables us to discover, and often predict, where attacks are staged and will emerge before they even launch.
Why keep firewalls and antivirus at all?
Once we prove our effectiveness, we are often asked: “can we get rid of our firewall or antivirus solutions?” While these existing defenses cannot stop every attack, they are still useful—if not critical—in defending against multi-step attacks. A big reason is threats never expire—every piece of malware ever created is still circulating online or offline. Signature-based solutions are still effective at preventing most known threats from infecting your systems no matter by which vector it arrives: email, website or thumbdrive. And firewalls are effective at defending both within and at the perimeter of your network. They can detect recon activities such as IP or port scans, deny lateral movements by segmenting the network, and enforce access control lists.
“One of AV’s biggest downfalls is the fact that it is reactive in nature; accuracy is heavily dependent on whether the vendor has already seen the threat in the past. Heuristics or behavioral analysis can sometimes identify new malware, but this is still not adequate because even the very best engines are still not able to catch all zero-day malware.”
Your Solution:
Re-balance investment of existing versus new defenses:
Here are a couple examples of how many customers free up budget for new defenses.
• Site-based Microsoft licenses entitle customers to signature-based protection at no extra cost. Microsoft may not be the #1 ranked product, but it offers good protection against known threats. OpenDNS defends against both known and emergent threats.
• NSS Labs reports that SSL decryption degrades network performance by 80%, on average. OpenDNS blocks malicious HTTPS-based connections by defending against attacks over any port or protocol. By avoiding decryption, appliance lifespans can be greatly extended.
“OpenDNS provides a cloud-delivered network security service that blocks advanced attacks, as well as malware, botnets and phishing threats regardless of port, protocol or application. Their predictive intelligence uses machine learning to automate protection against emergent threats before your organization is attacked. OpenDNS protects all your devices globally without hardware to install or software to maintain.”