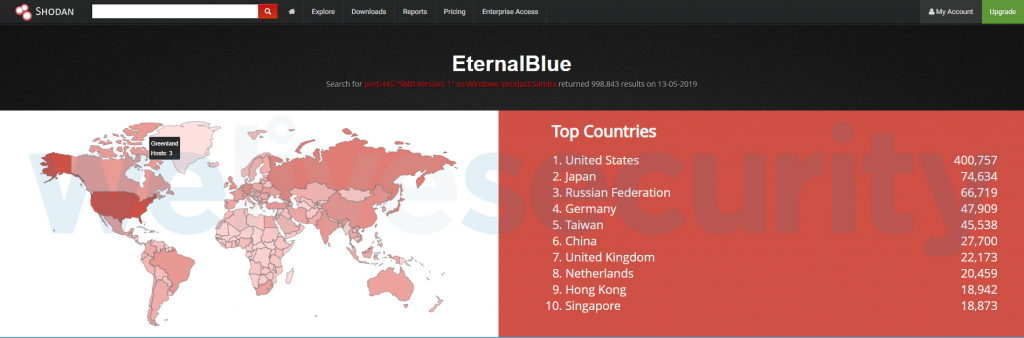
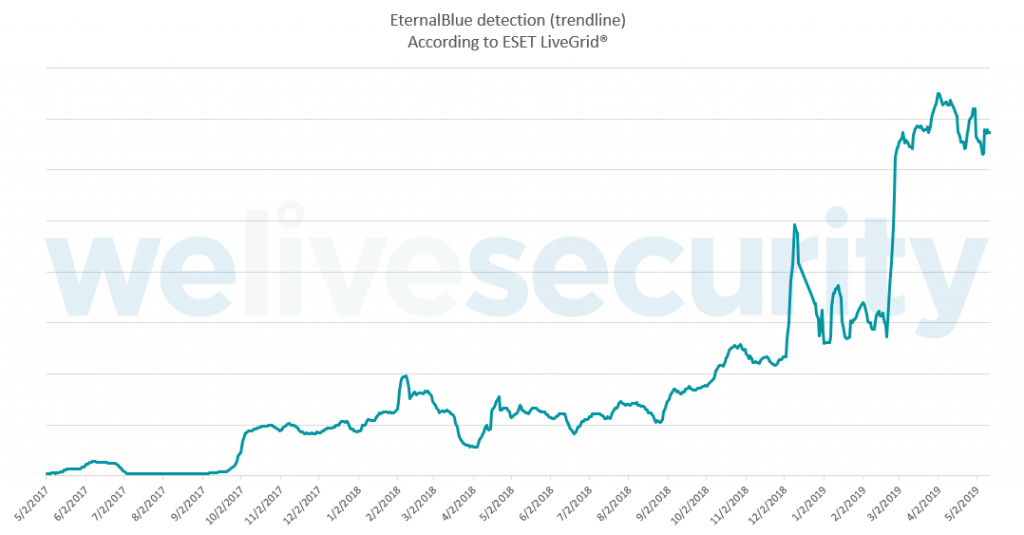
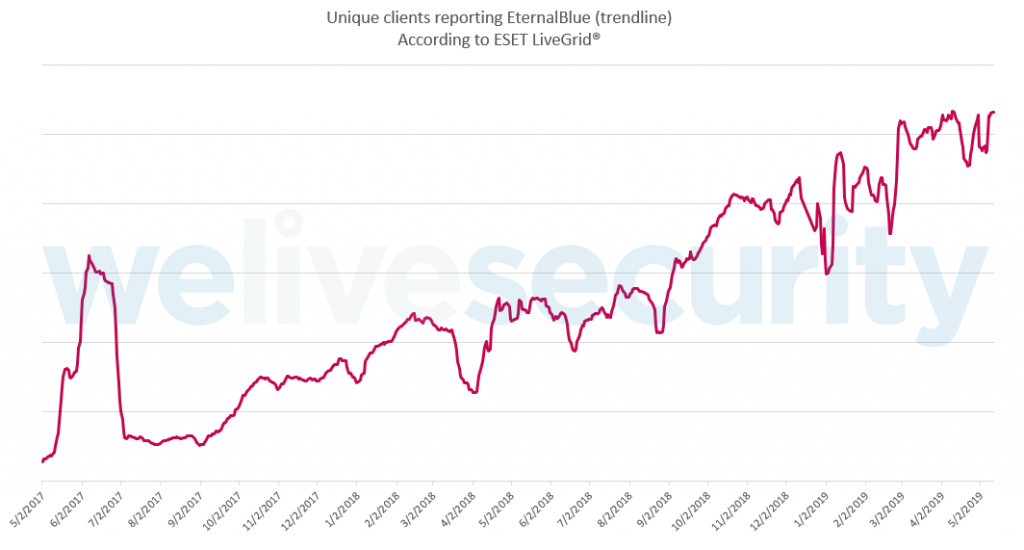
Decoding the vCenter Server Lifecycle: Update and Versioning Explained
Have you ever wondered what the difference is between a vCenter Server update and a patch? Or between an upgrade and a migration? Why don’t some vCenter Server versions align? Keep reading for the answers!
Version Numbering
The first thing you should understand is vCenter Server versioning. When reviewing your vCenter Server version’s you may see many different references to versions or builds.
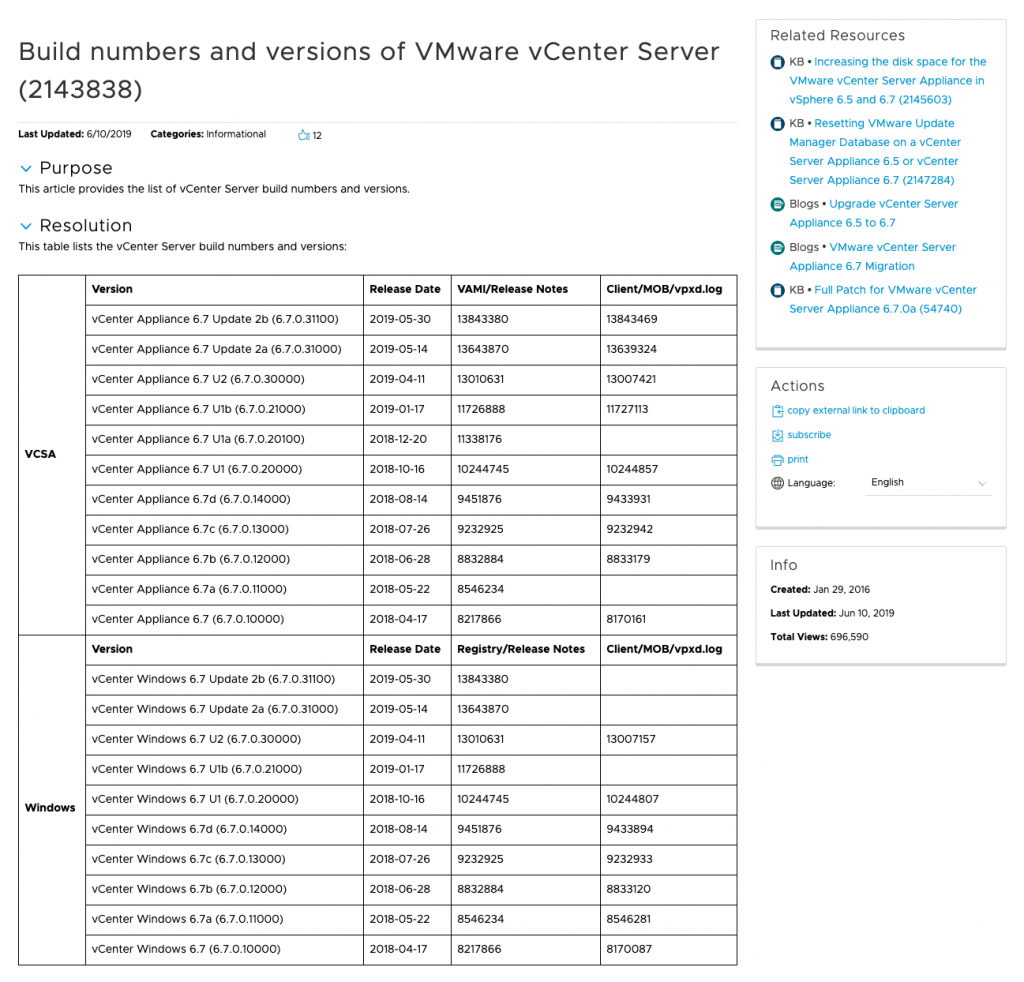
One of the first places you will notice a version identifier, is in our release notes. Here you will see the product version listed as vCenter Server 6.7 Update 2a and the build number listed as 13643870.

Once you have upgraded or deployed your vCenter Server you will see version identifiers such as 6.7.0.31000 listed in the VMware Appliance Management Interface (VAMI). You will also see a build number, such as 13643870.
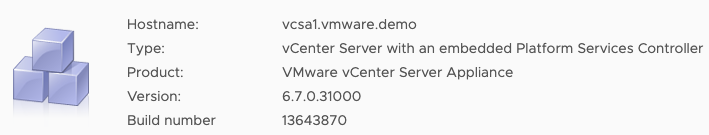
If you review the version information within your vSphere Client you will see the version listed as 6.7.0 and the build as 13639324.

The reason you will see differing versions among these places are because the release notes show the vCenter Server build and full release name, in the VAMI it will show the vCenter Server Appliance version in addition to the build and in the vSphere Client it will show the vCenter Server version and the build of the vSphere Client.
KB2143838 is a great resource that will explain the breakdown of versioning and builds for all vCenter Server versions.
Now that we have explained the way versioning works, let’s jump into the different scenarios where VMware will increment a version.
vCenter Server Updates and Patches
What is a vCenter Server Update and how does It differ from a patch?
A vCenter Server Update is one that applies to the vCenter Server application. An update can include new features, bug fixes or updates for additional functionality. vCenter Server updates will have a dedicated set of release notes and will be hosted on the my.vmware.com download portal.
A vCenter Server patch is more much streamlined as these are associated with operating system and security level updates. There are no application related changes, and these can target Photon OS, the Postgres DB, Java versions and any other supporting Linux libraries on the vCenter Server Appliance.
A vCenter Server patch also has no dedicated release notes as these are part of the rolled up VMware vCenter Server Appliance Photon OS Security Patches. Patches are also not stored on the my.vmware.com download portal but on the alternate VMware Patch Portal. It is also very important to note as listed in the release notes, these should not be used for any deployment or upgrade. The only reason the vCenter Server ISO’s are hosted on the VMware Patch Portal is to be used to restore your vCenter Server Appliance if using the built-in File-Based Backup. Patches can also only be applied within one and the same update release. So for example if you are currently on 6.7 Update 1 you would not be able to patch directly to 6.7 Update 2b , you would first update to 6.7 Update 2a and then patch to 6.7 Update 2b.
Now that we have explained the differences between a vCenter Server update and patch we can review the differences between an upgrade and migration.
vCenter Server Upgrades and Migrations
In its simplest form a vCenter Server Upgrade is defined as doing a major version change between vCenter Server Appliance versions. If you are running the vCenter Server Appliance 6.5 in your environment and move to vCenter Server Appliance 6.7 this would be considered an upgrade.
A vCenter Server migration is defined as doing a major version change between vCenter Server for Windows and the vCenter Server Appliance. If you are running vCenter Server for Windows 6.5 and move to the vCenter Server Appliance 6.7 this would be considered a migration. It is not supported to do a migration between the same major version as it consists of both a change of platform and an upgrade together.
In vSphere 6.5 and 6.7 an upgrade or migration of the vCenter Server is not completed in place. During the upgrade process a brand new appliance of the newer version is deployed, and based on the settings defined the data is exported from the old version and imported into the new one retaining the same FQDN, IP, Certs and UUIDs.
A back-in-time upgrade restriction is when you are unable to upgrade from one 6.5 release to another 6.7 release. For example, Upgrade from vSphere 6.5 Update 2d to vSphere 6.7 Update 1 is not supported due to the back-in-time nature of vSphere 6.7 Update 1. vSphere 6.5 Update 2d contains code and security fixes that are not in vSphere 6.7 Update 1 and might cause regression. When performing vCenter Server upgrades and migrations it’s also very important to pay attention to unsupported upgrade paths which are normally restricted due to being a back-in-time upgrade. It is also important to note that just because two releases might have the same release date, does not mean that they will be compatible. The best resource to review supported upgrade paths will be in the vCenter Server Release Notes section titled Upgrade Notes for this Release.

Resource Wrap-Up
- Build numbers and versions of VMware vCenter Server (2143838)
- vSphere Back-in-time release upgrade restriction (67077)
- VMware Patch Portal
- vCenter Server 6.5 Photon OS Security Patch Release Notes
- vCenter Server 6.7 Photon OS Security Patch Release Notes
- vSphere Central – Upgrade Resource Center
Conclusion
Versioning of a complex product can be difficult, but hopefully you now have a better understanding of what these numbers mean. If you have any questions feel free to post a comment below or check out any of the resources linked.
This article was provided by our service partner : Vmware