Managed service providers (MSPs) are playing an increasingly critical role in helping businesses of all sizes realize their digital transformation aspirations. The extensive offerings made available to businesses continue to allow them to shift day-to-day management onto you, the MSP, while allowing them to focus on more strategic initiatives. One of the most notable services being backup and recovery.
We introduced Veeam Availability Console in November 2017, a FREE, cloud-enabled management platform built specifically for service providers. Through this console, service providers can remotely manage and monitor the Availability of their customer’s virtual, physical and cloud-based workloads protected by Veeam solutions with ease. And, in just a few short months, we’ve seen incredible adoption across our global Veeam Cloud & Service Provider (VCSP) partner base, with overwhelmingly positive feedback.
Today, I’m happy to announce the General Availability (GA) of Veeam Availability Console U1, bringing with it some of the most hotly requested features to help further address the needs of your service provider business.
Enhanced Veeam Agent support
The initial release of Veeam Availability Console was capable of monitoring Veeam Agents deployed and managed by the service provider through Veeam Availability Console. New to U1 is the ability to achieve greater insights into your customer environments with new support that extends to monitoring and alarms for Veeam Agents that are managed by Veeam Backup & Replication. With this new capability, we’re enabling you to extend your monitoring services to even more Veeam customers that purchase their own Veeam Agents, but still want the expertise that you can bring to their business. And yes, this even includes monitoring support for Veeam Agent for Linux instances that are managed by Veeam Backup & Replication.
New user security group
VCSP partners wanting to delegate Veeam Availability Console access without granting complete control (like local administrator privileges) can now take advantage of the new operator role. This role permits access to everything within Veeam Availability Console essential to the remote monitoring and management of customer environments (you can even assign access to your employees on a company-by-company basis), but excludes access to Veeam Availability Console server configuration settings. Now you can assign access to Veeam Availability Console to your staff without exposing settings of the Veeam Availability Console server.
ConnectWise Manage integration
We’re introducing native integration with ConnectWise Manage. Through this new, seamless integration (available in the plugins library tab), the management, monitoring and billing of Veeam Availability Console-powered cloud backup and Disaster Recovery as a Service (DRaaS) can now be consolidated with your other managed service offerings into the single pane of glass that is ConnectWise Manage. This integration makes it easier and more efficient to expand your services portfolio while making administration of multiple, differing managed services much more efficient.
Matt Baldwin, President of Vertisys said, “This integration is exactly what my business needs to streamline our managed backup and DRaaS offering. The interface is clean and intuitive with just the right number of features. We project a yearly savings of 50 to 60 hours.”
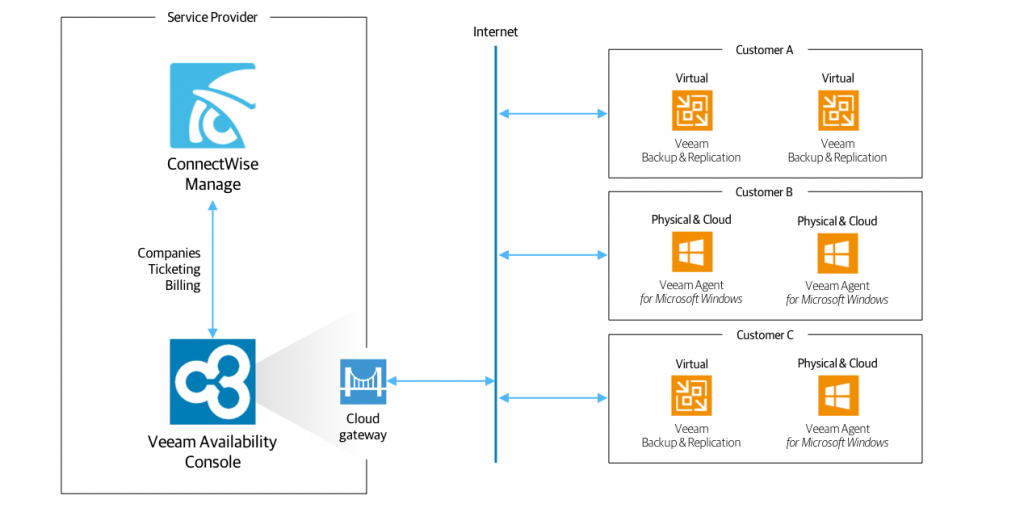
Let’s take a closer look at some of the integration points between Veeam Availability Console and ConnectWise Manage.
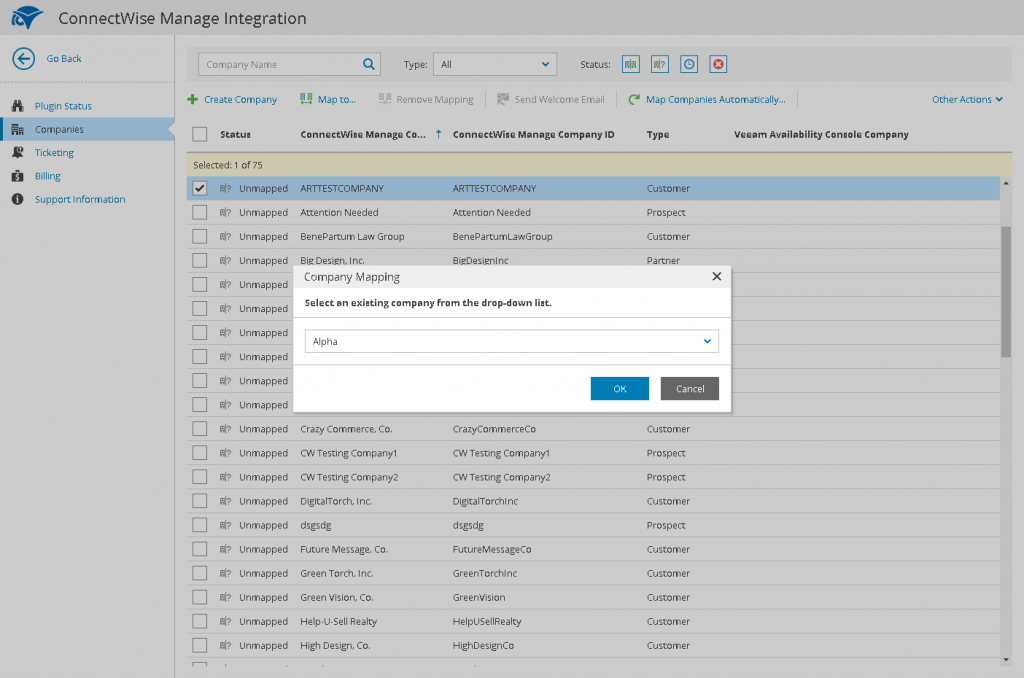
Mapping companies
Firstly, the integration will help avoid a lot of manually intensive work by automatically synchronizing and mapping companies present in ConnectWise Manage with those in Veeam Availability Console. Automatic mapping is achieved through the company name. Before mapping is fully-complete, Veeam Availability Console allows you to check over what it’s automatically mapped before committing to the synchronization. If no match is found, mapping can be completed manually to an existing company or through the creation of a new company, with the option to send login credentials for the self-service customer portal, too.
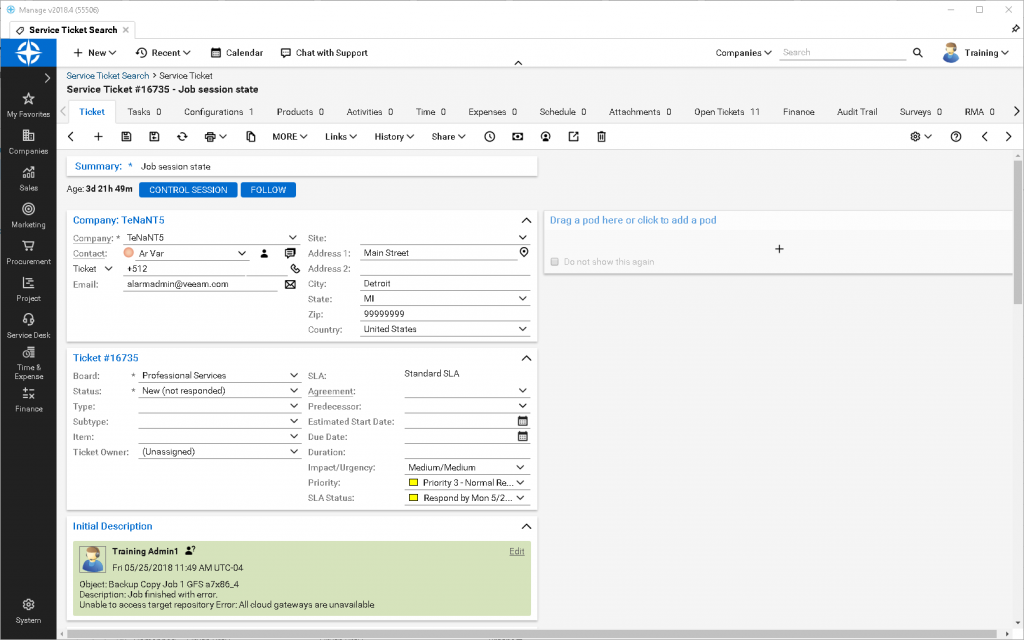
Ticket creation
The integration also enables you to more quickly resolve issues before they impact your customers’ business through automatic ticket creation within ConnectWise Manage from Veeam Availability Console alarms. You can specify from the list of available alarms within Veeam Availability Console all those that are capable of triggering a ticket (e.g. failed backup, exceeding quota, etc.), and to which service board within ConnectWise Manage the ticket is posted. We’ve also enabled you with the capability to set delays (e.g. 1 minute, 5 minutes, 15 minutes, etc.) between the alarm occurring and the ticket posting, so issues like a temporary connectivity loss that self-resolves doesn’t trigger a ticket immediately. Every ticket created in ConnectWise Manage is automatically bundled with the corresponding configuration, such as representing a computer managed by Veeam Availability Console. This makes it incredibly easy for support engineers to find which component failed and where to go fix it. The integration also works in reverse, so that when tickets are closed within ConnectWise Manage, the corresponding alarm in Veeam Availability Console will be resolved.
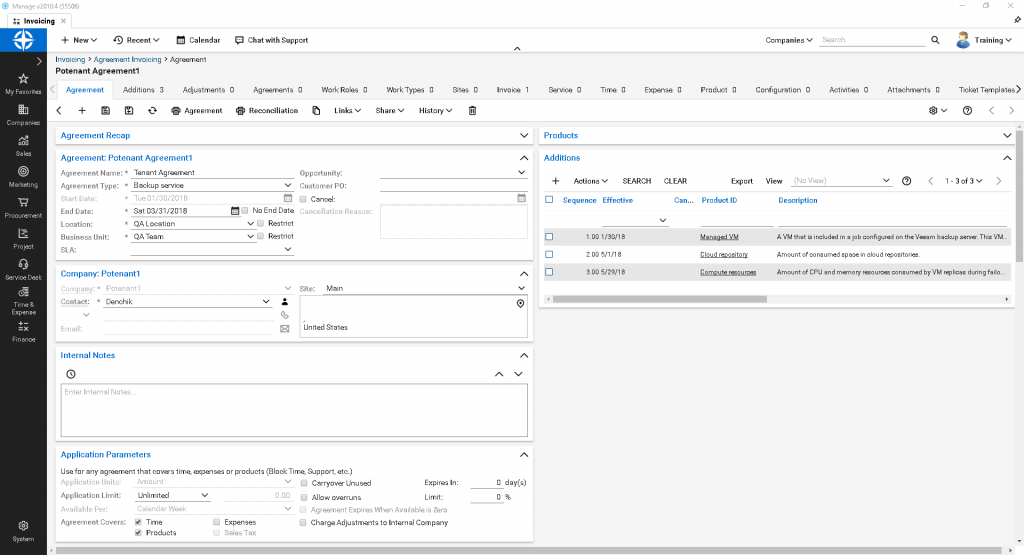
Billing
The final part of the integration extends to billing, reducing complexities for you and your customers by consolidating invoices for all the managed services in your portfolio connected to ConnectWise Manage into a single bill. Not only this, but the integration allows for the automatic creation of new products in ConnectWise Manage, or mapping to existing ones. Service providers can select which agreement Veeam Availability Console-powered services should be added to on a per-customer basis, with agreements updated automatically based on activity, quota usage, etc.
Enhanced scalability
Finally, we’ve enhanced the scalability potential of Veeam Availability Console, enabling you to deliver your services to even more customers. The scalability improvements specifically align to the supported number of managed Veeam Backup & Replication servers, and this is especially useful when paired with the enhanced Veeam Agent support discussed earlier. This ensures optimal operation and performance when managing up to 10,000 Veeam Agents and up to 600 Veeam Backup & Replication servers, protecting 150-200 VMs and Veeam Agents each.
This article was provided by our service partner : veeam.com